Models for Threat Intelligence
Table of Contents
1. MAIF Lecture 2
- Class: Malware Analysis and Incident Forencsis
- Topic: Threat Intelligence
2. Model for Threat Intelligence
How we can decide effective contermeasures if we don’t know how the attacker will attack, considering that he can use different approaches and techniques. This problem can be address by using cyber thret intelligence. It consists on profiling the adversary; clearly this kind of activity is not easy.
We want to make the most out of the scarse information that we have to make good decisions.
2.1. Information
The information that we can collect can come from different sources: malware, monitoring tools (IDS, HIDS), logs from firewalls, application servers, OSs, and VPNs; we may also have information coming from external sources like public or private repositories.
This huge set of heterogeneous information can be:
- Loosely structured, or
- Strictly structure
- Low level, very technical information
- High level written in natural language
Leaving it as it is very difficoult to use, thats because at each phase of the attack a trace will be left by the attacker, each trace its present in different subsystem, and only by putting togheter all of them it is possible to construct the full story of the attack. Most of the time the analyst can produce just a credible hypothesis that will allow us to make decisions on what to do next. We need to deploy an intelligence process, an its goal is to analyze data in order to extrace actionable intellingence. Actionable intelligence is a bit information that allows us to make useful decisions.
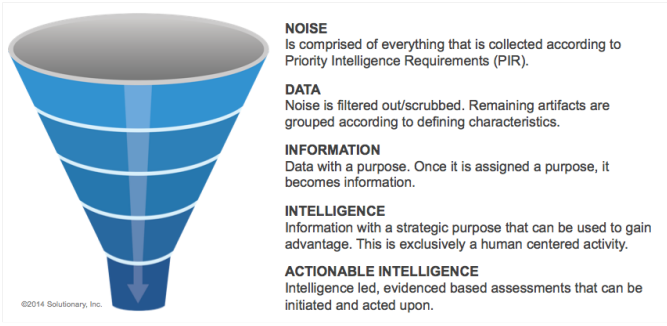
From the first huge set of data collected, called noise, we have to extract only the elements that are potentially relevant to the job. The extracted information is called Data, they can be organized in different groups; and then we can extract a subset of data with a specific purpose to extract a set of Information, the purpose allows us to restrict the reasearch to a subset of data. The Information extracted still has a problem: it is made up by independent pieces, so the goal of the next phase is to collect the dots: identify what is relevant and how the single bits play a role in our attack hypothesis. We have to associate pieces of information to the parts of an hypothesis to give a strategic purpose to the information collected; for example discovering that a user compromission has taken place. The subset of information that has a strategic relevance is an Intelligence, this is exclusively a human center activity. Clearly the distilled elements of intelligence tells something about how an attacker acted against us, and if we can use the intelligence to understand how a successful attack happenend we can act to defend us in the future; this subset of data is called Actionable Information.
The complexity of this process is high, and it is not just a simply seuence of steps. In reality it is an iterative process.
2.2. Threat Intelligence Process
The intelligence cycle is made up of five steps:
- Collection
- Processing
- Analysis and Production
- Dissemination
- Planning and Direction
By iteratively collecting, analyzing, extracting information it is possible to better direct subsequence cycles of intelligence. We should start to try at identified the attackers, it does not mean to perform attribution, but to identify a specific source that uses specific techniques that is playing against us. For example if we see that an attacker uses different strategies and approaches can help us to understand the number of his goals. The next step is to profile the attacker, trying to pinpoint his motivations to identify his key tactics that is willing to use against us. This means that we are reversing what the attacker did during his recoinessance phase, so if we are able to identify this key tactics to reverse engineer his intentions.
The playbook represent for the attacker the instruction manual to perform the attack, so from the analyst point of view it is useful to rebuild the playbook because we can setup the perfect protection for that attack because for each step of the attack we can mitigate it or block it. Of course in reality our ability to rebuild the playbook is only partial, but it represent the foundamental protection step of our conceptual strategy.
The next step is to understand how this conceptual approach can be put in place. At each level of the process there are differnet goals:
- Tactical Level. Composed by the people working at the SOC, their goals is to provide technical decision to provide understanding of how mitigate threats and enable tools to do the heavy lifting: very practical actions that can be taken quickly and have an impact on the security of the system.
- Operational Level. At this level the management decisions are taken, those decisions will provide long term actions; the goal here is to enable the formulation of approaches to dealing with threats and prioritization of team activity.
- Strategic Level. At this level decision are taken by the board of directors, and usually they regard budget allocation, and are correlated to the business impact.
At each level the time frame of decision making increase.
2.3. How to make intelligence actionable?
We are able to take actionable intelligence only if we are dealing with budget constrained attackers or rational human attackers; We assume that the attacker will find the best possible attack path that maximize its likelihood of success while minimizing the costs of the attack itself. In the end the only long term strategy is trying to increas the cost of the attack while reducing the cost of defense.
The cost factor may depends on: expertise, time, budget, and resources that he can access. From this point of view we can also assume that the attacker will work as a “good engineer”, so he will make sure that each tool built, will be as much as possible reusable and scalable. So an atack will have two features:
- Repeatability
- Scalability
Taking into account this characteristics we can determine that attackers will determine the least costly and most valuable attacks based on factors such as who the targets are, required success rate, and spread of conversione:
| Inexpensive, valuable, scalable, repeatable | Costly, valueless, unscalable, unrepeatable |
|---|---|
| Phising | We vulnerabilities |
| credential reuse | 0-day exploits |
| Know vulnerabilities w/ public exploits | Know vulnerabilities w/ out exploits |
3. Intrusion Killchain
The Attack Killchain is a way to unroll the phases of an attack, at the same way we can use an intrusion killchain to represent a methodology to analyse tentive of intrusion to extract actionable intelligence. It is a starting point that tells us the order of events of the collected evidences.
4. Indicators
Indicators are foundamental element of intelligence, they are any piece of information that objectively describes an instrusion. There are three types of indicators:
- Atomic. Like an IP address; they can’t be broke down in smaller parts.
- Computed. This kind f indicator are derived from data incolved in an incident. For example the MD5 hash of a sample.
- Behavioral. As the name suggest they are sets of other indicators, that are put togheter in a human readable sentence and subject to qualification by quantity and possibly cobinatorial logic. They represent they way of the attack is behaving in our system.
The behavioral indicator is more important than the others because a collection of behavioral indicators is a subset of the attacker playbook that we want to rebuild. All the indicators are pieces of actionable intelligence, but the impact of the usage of different indicators on the attacker can be quite different.
Once we idnetify an identicator we have to understand which is its role inside the attack. When we analyze an incident, we’ll quickly come up with a lot of atomic indicators, that they can be useful to put in place easy countermeasures, then we have to understand which phase of the attack generate each atomic indicator with the pupose of constructing a behavioral indicator.
4.1. Life Cycle
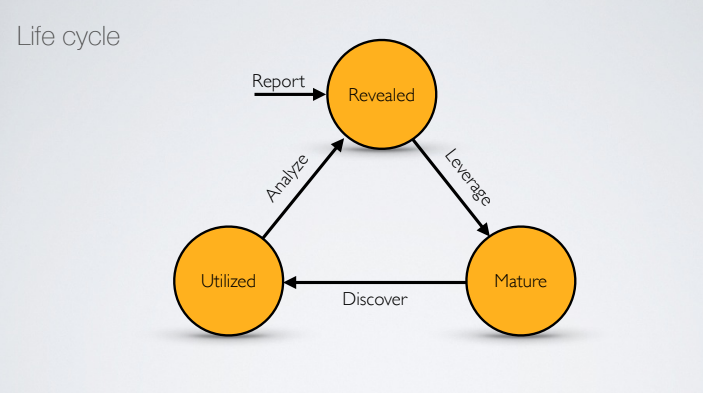
Once an indicator is reported, it becames revealed. Once an indicator is revealed it can be leveraged to increase the maturity level of the security. It may happen that once an indicator is leveraged we discover that there is an ongoing attack that utilized that indicator. At this point the indicator becames utilized because we utilized it to discover an attack. Then we analyze the attack improving the knowlendge revealing new indicators.
4.2. Indicators role in the Intrusion Killchain
Inficators can be used to describe.identify various stage of the intrusion using the kill chain as a reference model.
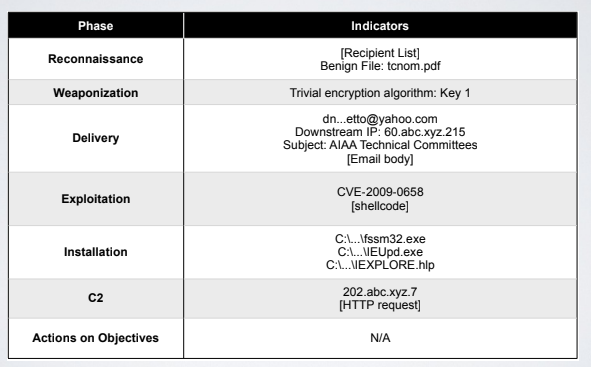
This example exaplain how it is possible to proceed step by step to identify and map the indicators to the intrusion killchain. This approach will not explain all the attack but it is a good starting point; for example we miss some information, like: who is the attacker, and which was the pupose of the payload.
We can use these information for setting up new monitoring rules: on mail server, update host based IDS, update network based IDS and more. The attacker will try to change the delivery phase of the attack to persist its attack, changing the minimum amount of parts of the attack.
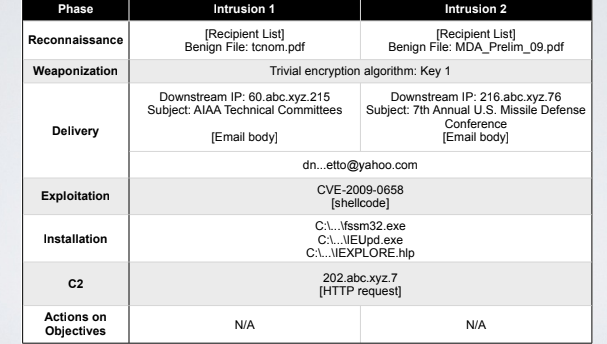
In the above example, the attack is blocked during the exploitation phase because, in the previuos attack we updated the host based IDS to catch the exploitation of CVE-2009-0658.
The attacker may try to change some other aspects of the attack, because our protection strategies changed the attack surface. By looking at the different phases of an attack what we want to identify are commonalities between tentative of intrusion.
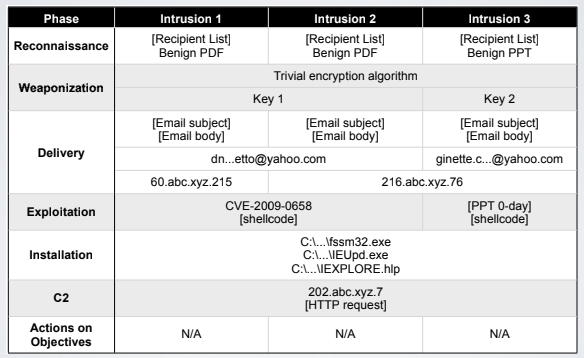
For example in this case he’s using the same trivial encryption algorithmn, and the C2 ip address is the same. These commonalities represent the footprint of the attacker, characterising the adversary. The pattern extracted can be used to uniquely identify the adversary. The best countermeasures are those which block the commonalities of different attacks from the same adversary.
Our behavioral profile is set up by intentifing the connection points between different intrusion tentatives.
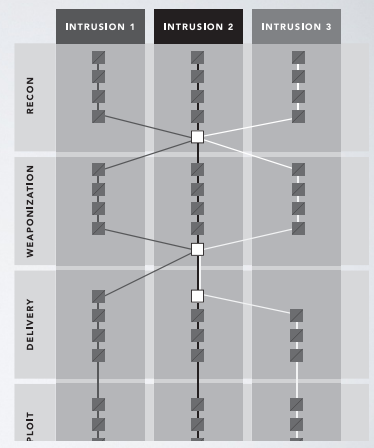
The data used can come from previous intrusions, and public cyber threat feeds. The profile can also be used for attribution purposes.
5. Course of action
We can use the indicators obtained and the instrusion killchain to align defensive capabilities to each specific step planned by an attacker.
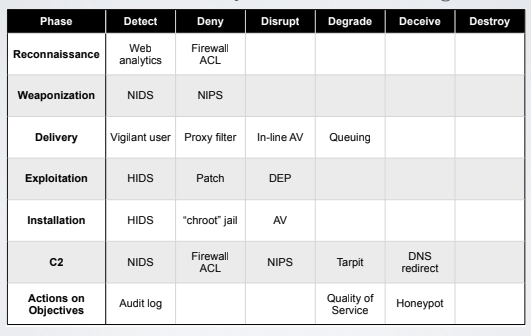
The actions to counteract intrusion are:
- Detect: set up detection rules of an indicator for future events.
- Deny: prevent it from taking place.
- Distrup: make the event fail as it is occurring.
- Degrade: slow down the further actions of the attacker; For example throttling bandwidth.
- Deceive: are usually connected to the usage of honeypots. Instead of blocking their action the action is diverged to another target. Honeypots are used to understand the techniques and the obectives of an attacker.
- Destroy: offensive action against the attacker.
Of course sometimes a strategy does not fit in a single category, for example DoS contermeasures can be cosnidered as deny and degrade countermeasures.
For example for the exploitation part the usage of that exploitation code it can be identified by an host based IDS, can be denyied by patch, or can be destroyed by an antivirus software.
Measure effectiveness will drive defensive strategies over time and can be done if there is a clear and organized plan that explain why a specific countermeasure is used. The course of action as to be carefully organized and maintened over time.
6. Reconstruct the Killchain
An improved protection affects the course of actions; from a late phase detection to an early phase detection. The early phase detection is an indicator of the good implementation of protection measures.
The traces left by the first attack tentative are used to block a new attack in a earlier phase. When we consider an attack to collect indicators about it, we have to analyze everything we can observe, then for the part that we can’t observe we have to use a synthesis process to try to understand how the attack would unfold; in this phase we’ll use our hypothesis.
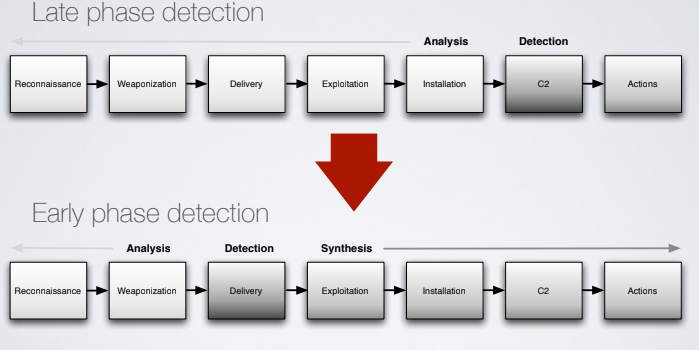
The more we are good in preventing attacks, the less information we’ll obtain further information about the attacks. The result is a reduction of effectiveness if preventing new attacks. In the end each attack will help preventing furhter attacks from the same source, so the objective is to became really smart in preventing the next move of a known adversary.
7. Pyramid of Pain
There are different kind of indicators, to understand how much an indicator is useful we have to consider different factors.
Briefly we can say that an indicator is useful if it helps us to block an attack. But it is impossible to know it a priori. For this reason we can consider how much the attacker is willing to invest in changing his strategy to use a different indicator. If an attacker is not willing to invest to change a particular aspect of the attack the value of the indicator related to that aspect is higher.
Looking at the content of identicators we may identify different kinds of indicator:
- Hash Values, that can be used to uniquely reference to a specific sample of a malware or files involved in an intrusion.
- IP Addresses
- Domain Names
- Network Artifacts. Assuming that we are able to observe that a malware communicate with a C2 via a specific pattern, the characteristics that compose the pattern can be used to build rules that impact in a huge way the attacks strategy. Some useful information can be: URI patterns, C2 information embedded in the network protocols, distinctive HTT PUser-Agent and more.
- Host Artifacts
- Tools
- Tactics, Techniques and Procedures. TTPs represent the final point of the defense journey, it is the set of actions that the adversary takes to accomplish his mission, from reconnaissance all the way through data exfiltration and at every step in between.
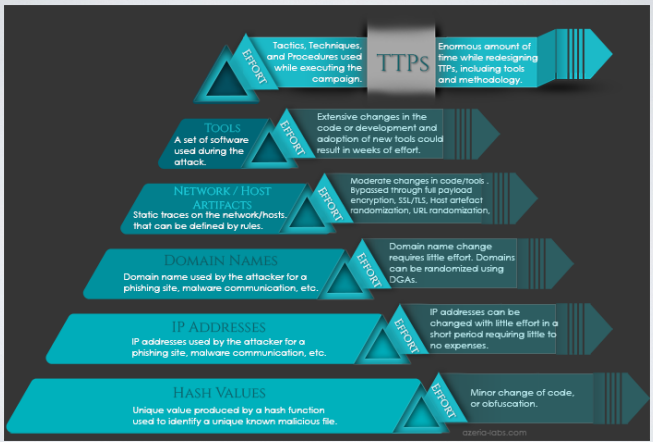
In the bototm we have the less reusable indicators, so the indicators of which the attacker will have less costs in changing them. On the top of the pyramid there are the TTPs, to change TTPs the attacker will incur in huge expenses.
7.1. Limits
At this stage we used the killchain to organize all our contermeasures and to understand how the attacker proceed during the attack; the problem is that the limited number of steps is not enough to increase the level of detail. For this reason there are complementary models that can be used togheter to increase the level of detail, maybe reasoning on the intersection of each indicator. For example a strong limitaiton of the killchain is the difficoulty of identifying gaps.
8. Diamond Model
It is based on the idea that every incident can be represent as a sequence of events. Each event represent a specific phase of the attack and generate indicators that can be collected target side. Different events during an attack can be connected in a meaningful way creating an activity thread. Different threads composed by common events may represent activity groups (incident with elements in common).
8.1. Event
An event is a part of an intrusion, and it is represent by a set of core feature, they pertain to few fundamental aspects:
For every intrusion event there exists an adversary taking a step towards an intended goal by using a capability over infrastrcture against a victim to produce a result.
The adversary may also require access to further external resources to fullfill its goal (meta features).

The interesting aspect of the diamond model is that it provides a mapping on how the features interacts togheter:
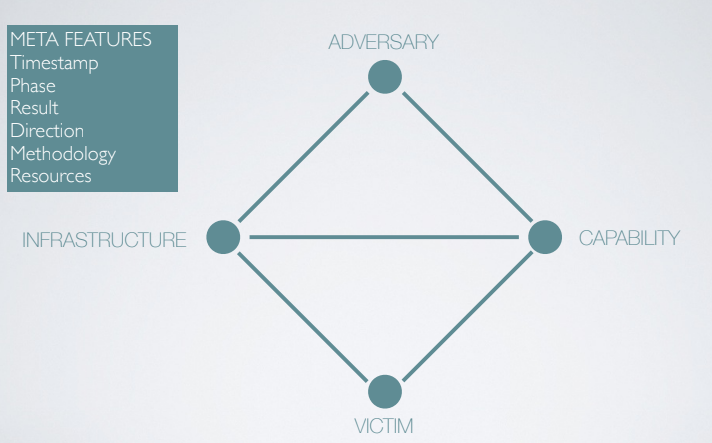
The adversary interaction with the victim is mediated via the capabilities and the infrastructure, it is never direct; at the same time the interaction between the infrastructure and the cabapility is very tight.
The idea of the Diamond Model is to provide an approach to observe data and extract intelligence to identify gaps to improve the ability of extracting further useful data: planning and direction phase of the intelligence cycle.
Beside the core feature the diamond model allows to describe additional features useful to better describe the attack; meta feature are not organized in an organized way; they are simply a list grouped in cluster.
8.2. Adversary
The feature related to the adversary help us to better describe the actor/organisation responsible of the attack.
8.3. Capabilities
The capabilities are all the tools and technique that the adversary can use against the victim. The capability capacity is the sett of all the vulnerabilities and exposures that can be utilised by the individual capability regardless of the victim. The arsenal is the complete set of tools that and adversary has.
8.4. Infrastructure
The capabilities must be supported by an infrastructure, it describes the physical and logical communciation structure used by the adversary to deliv a capability. The infrastructure can be directly controlled, provided by an intermediary, or a straight public infrastructures. In the last case the attacker creates efimeral accounts on cloud providers.
8.5. Victim
The victim can represent different kind of elements, typically the victim is the full organization, but when modelling a specific event we can resize the scope of the victim to a specific host inside a subnet. The vulnerability used to attack the vicitim is one of the sub-features of the victim. When using the diamond model full precision is not that important, is better to make the best from the information acquired.
8.6. Meta Features
Meta Features are not strictly organized, for example we can use the timestamp of the event, the phase of the killchain at which the event belong, and the results of the operation perfomed by the attacker. When applying this model in the real world, the Threat intelligence team performs the analysis procedures using a software to collect information, so is the software platform that provides a way to organize the features on top of the model. The way in which all these features are represent on a technical standpoint also depends on the platform used, many organization builds their own platforms.
8.7. Extensions
While there is a technological link between capabilities and infrastructure the diamond model does not include a specific link between the adversary and the victim; it is the motivation of the adversary, but this link exists at high level. The problem is that not necessarly the motivation is discoverable or known, and if a single phase of the attack is considered is difficoult to find a relation between the victim and the adversary.
8.8. Usage
Differently from the kill chain integrare reg
The discovery of a specific feature, helps the further steps of the investigation thanks to the connections between the core features provided by the model. Thats the main difference between the killchain model and the diamond model: it provide precise indications on what to look for; so it can be used operatively in order to drive the threat intelligence process.
The model is not used to describe a full attack, that’s because an attack is a process that evolves is several steps, some of them are iterative and other are inteleaved. Modelling a full attack we’ll produce a cluttered view of the attack, for this reason the diamond model can describe the relationships among the features that represent an attack, and can be used togheter with the kill chain model as an activity thread:
- Small events within an icident are mapped with diamonds
- Each diamond is put in a specific phase of the kill chain model
- Different diamonds are related with each other, the links may be not obvious.
Another importan advantage of this approach is that, now we have a specific indication of the relationships between the indicators in the different phases and/or in the same phase, providing an effective way of communicating how the incident has evolved.
Once a collection of threads has been acquired the final goal is to use the information to find commonalities and understand where to look for further information and check for gaps to understand events that were not correctly identified. Vertical correlation can be used to find gaps, horizontal correlation can be used to find commonalities between different threads; the gaps underlined after this process can possibly highlight the parts of the intelligence process that need an improvement.
If the last diamond of a thread is linked to a diamond on the top of another threat we can think that the two incidents are part of a multi-step attack. In a lot of practical cases as soon as the attacker is able to overcame the border defenses of the organization he reaches a point at which the recoinessance targets internal hosts that are not hardened as host exposed on the internet; for this reason a defense in depth approach must be used, in such a way each defense border inside the domain as to be hardend like the external border.
After describing in detail different events with different Activity Threads there the need to clean all the low level indicators, and distill high level TTPs that are represent by few diamond over few phases of the kill chain. With the diamond model it is possible to map the TTPs to other model that represnet how the system can be attacked via an attack graph: it represent all the possible activity threads, and can be considered as a large collection of hypothesis. In this way it is possible to identify all the possible targets of the attacker inside the system and what should must be done to reduce the success probability of the attacker.
8.9. Activy Groups
The idea of activity group is to create an organized and searchable database that collect all the information gathered. Each activity group groups activity threats characterized by some commonalities. The creation of an activity group is composed of different steps:
- Define an analytic problem
- Select Features used to form the basis of classification and clustering
- Create activity groups from the set of events and threads
- Growth
- Analyze the activy groups to address the analytic problem defined in step 1.
- From time to time the activity group must be Redefined to increase the accuracy.
Incoming events and threads can be used to increase the knowledge base of the activity groups in order to better understand and match the evolution of the adversary.