Attack Killchain
Table of Contents
1. Lezione 3 - Querzoni
- Class: Malware Analysis and Incident Forencsis
- Topic: The attack killchain
2. The Attack Killchain
Today all modern countries are going toward a new model of managment of cyber attacks. Most countries are building governament organization used to counteract in a coordinated manner cyberattacks; this shif in paradigm enabled a better information sharing infrastructure leading to better ways to counteract attacks.
3. The 5Ws of a Cyber Attack
3.1. Who
First we have to define the target, it is a single user, a whole industry sector (financial, health, energy, …), an industry sector or Military and Defense agencies. Common targets will be organization with huge financial situation like banks. At the same way public agencies and healthcare are common targets because they collect a lot of personal informations that can be sold on the black market.
Then we define the threat. Threats can be of different kinds. The real threats today comes from organized groups composed by different people with particular roles and skills. Mainly we talk about Cyberterrorists, Cyberwarfare and Hacktivists like anonymus.
The last actor in the killchain is represented by third parties; We’re talking about academic researchers, individuals and companies that perform researching in cybersecurity. Another important third-actor is represented by white-hat hackers. CERTs and governement agencies have the purpose of simplyfing the information sharing about cyberattacks in order to detect and respond better if future attack occurs.
3.2. Why
There can be different motivation behind an attack, but the most common one is financial. So the purpose of the attacker is to gain money.
3.3. What
The activities performed during a cyberattack varies a lot, ranging from data theft to physical damage, passing through financial fraud.
3.4. When and Where
Today there is no limit regarding this two aspects. Obiously we can observe that the attacks target rich countries more then poor countries.
4. Evolution of malware
The security of computer systems traces back to the birth of internet, but modern attacks start appearing around 1998: the Chernobyl Attack. In 1998 there were a lot of Antivirus companies that claimed to be able to detect every computer virus; so a taiwanese student wrote a destructive malware that rendered PCs unbootable. It spreads under the Portable Executable file format under Windows 9x and ME. In 2001 the Code Red attack took place; it targeted the U.S. governement websites, changing the homepage of the whitehouse website; it exploited a vulnerability in the Microsoft Internet Information Server. In 2003 was the time of the fastest spreading computer virus ever Slammer; it infected more than 75000 hosts in less than 10 minutesm it exploited a buffer-overflow vulnerability in computers on the internet running Microsoft’s SQL Server. It was not harmful but it caused an involuntary DDoS attack blocking Bank of America, 991 ER System and an Ohio nuclear plant. Other examples are represented by myDoom in 2004, and Poison Ivy in 2005 that is the first example of RAT (Remote Access Trojan) giving to the attacker full survellaince and control capabilities. In 2007 the Zeus malware apperead; it was designed to install a keylogger on victim’s system and was delivered through phising; the second version of the Zeus was capable of provide a lot of different features transforming Zeus in a pay to use service, as today it is the malware with most variants.
In 2008 there is aninteresting example of malware found in a USB stick in a military base: Agent.btz, it is one of the first of spyware in the real sense, and one of the first example of malware created to circunvent air-gapped networks.
4.1. Stuxnet
Stuxnet is the first example of cyber-weapon with unprecendented complexity, it was developed by the US to destroy the uranium enrichment plants of Iran. Like Agent.btz it’s belivied that it was delivered via thumb drives; the Payload was built to infect the SCADA appliances controlling centrifuges forcing them to spin outside nominal conditions for long periods while letting the control application showing nominal conditions. The malware has reduced the quality of the enriched uranium while damaging the instruments used to do so. Stuxnet used three zero-days, and was developed under high quality standards, like an industrial application. This let to the idea that it was developed by governamental agencies.
4.2. Digitar
Another interesting example is the so colled Digitar attack, in which several server of the Digitar root Certification Authority were owned by attackers, giving them the capabilities to issue hundreds of valid certificates. To avoid consequences the Diginator CA was blacklisted and it filled for bankruptcy a few months later. Another example of physical consequences of a cyber attack.
4.3. Flame
Flame is the first example of complex and modular malware used to perform different kind of targeted cyber espionage. It was designed with a fradolent certificate purpotedly from the Microsoft Enforced Licensing Intermediate certificate authority thanks to the use of a MD5 collision to build trustable certificates.
4.4. Wannacry and NotPeya
Most recent examples, they use advance exploits and are used in large-scale attacks. They are advanced enough to exfiltrate data while encrypting them to ask a twice ransom: one for decrypt the data, and one to not publish the stolen data.
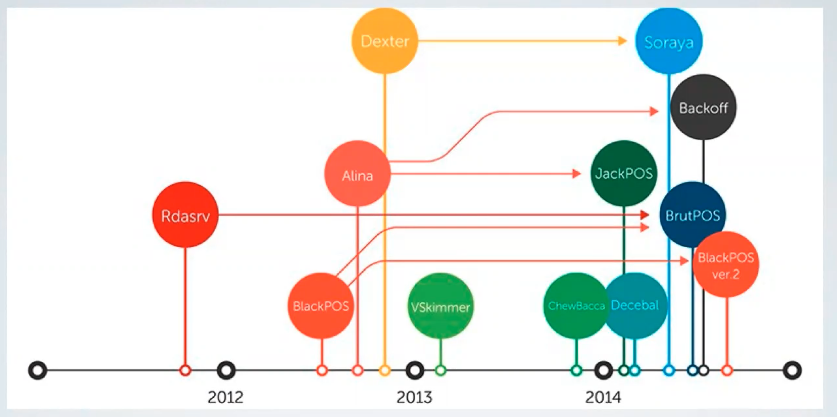
4.5. POS malware
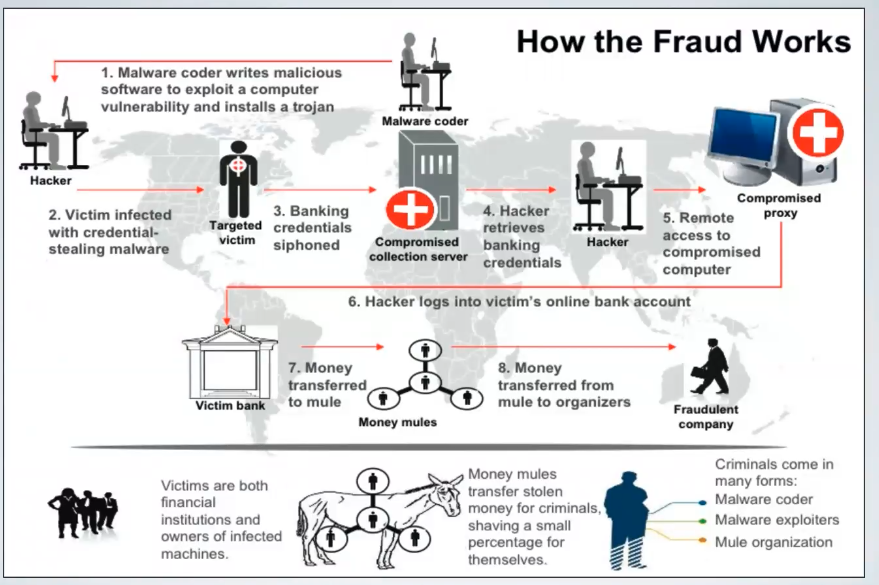
In the last years there was an increase of POS Malware; POS devices where designed to not soore credit card data and to encrypt credit card data when it is transmitted, but they did not protect data while it is processed; for this reason credit card data can be stolen from the memory while the transaction in ongoing.
5. Security Asimmetry
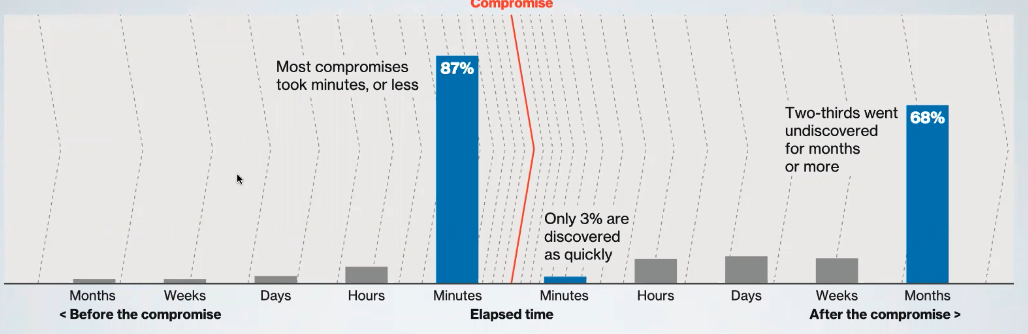
Today defending is way more expensive than attacking, this assimmetry in cost it is in part caused by the difference between discovery time and compromise time.
We have to work in order to reduce the probabilities of success of the attacker, increasing the difficulty of the attack there is an increase on the effort that the attacker has to put to perform the attack.
6. Anatomy of an attack
We may face attacks of very different nature, from targeted to mass level approaches. We are interested in attacks that have a precise targeting, that gives full control of target RAT, and a long term persistence (APT), so attacks in which the attacker wants to take full control of the victim and ensure himself a long persistence via opening multiple bakcdoors, perform obfuscation activities and evasion techniques.
To characterise this kind of attack we’ll use the Intrusion Killchain, to organize the technical contents of an attack in a standardadized way.
6.1. Reconnaissance
The reconnainssance phase is typically the first phase of an attack, during this phase the attacker studies his target with the objective to collect as many information as possible to find the most effective strategy to be implemented during the attack.
The adversary investigate the target nature finding its weak points definin the attack surface.
The attack surface is composed by all the points that the attacker can reach in his current position.
The attakcer will use public available sources like social media, public data source and similar. Some useful information are: the internet footprint of the company, contacts of the C level staff, and the mission and services offered by the company. This set of information compose the target surface.
The target surface can also be composed by the information of employees, data acquired from previous data breaches, and more.
In this phase the attacker will find a set of potential vulerabilities, and choose the one that represent the most effective entry point: the vulnerability that gives him an high success rate and at the same time that minimize the cost to perform the attack; assuming that the attacker is planning the attack as a rational human being: budget limited.
At the end of this phase the attacker will have the skeleton of an attack plan: potential access point(s) that he will try to exploit.
The Reconnaissance phase is widely underrated from the defender perspective, the denfensive options of this phase are limited, but it is possible to reduce the level of public available information, or at least try to control them. Of course hiding information will not make the system more secure, but will increase the cost of the attack.
6.2. Weaponization
In this phase the plan will be transoformed in something operational. The attacker will acquire and setup tools to implement the attack. This phase represent a technical challenge for the attacker. This phase can be less or more expensive depending on the implementation of the vulnerability that the attacker wants to use. Very often this phase is outsurced.
6.2.1. Software Vulenrabilities.
The final artifacts of software will implement a subset of the requirements, and will introduce undesired functionalities and introduce bugs. These two last aspects can lead to potential vulnerabilities.
A vulnerability can be a bug that the attacker can use to push the code to perform undesired actions.
New Vulnerabilities are discovered every day and are tracked in databases like NVD, they containt different kind of useful information about mitigation or possible patches.
Not all the vulnerabilities are the same, some of them are discovered by companies that discovers them for job, by attackers, software developing companies and sometimes also by users. The way on the vulnerability is discovered will change the number of incidents related to that vulnerability: if a vulnerability is published without first being patched the criminals will rush to create exploit code trying to compromise as most machine as possible.
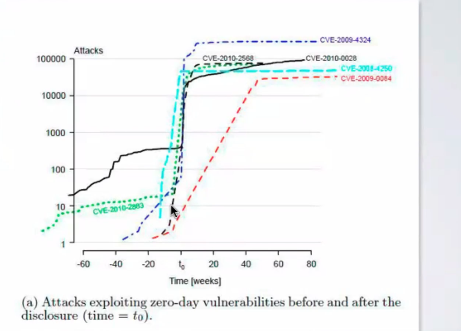
During the weaponization phase the role of vulnerabilities is important, a lot of atttacks today uses old vulnerabilities, thats because we assume that a patch will completely remove the vulnerability; of course not all the users will apply the patch at the same time; there also cases in which a patch can’t be applied, for example in legacy systems.
6.3. Delivery
The weaponized software as to be delivered to the target machine. As today the most used delivery method is phishing. Spear phishing is phishing specially crafted for a target, that is much more difficoult to be recognized as phishing.
Delivery vector can be an EXE file, JS code, ZIP files or DOC, XLS and PDF documents. THe exploit code as to pass undetected as possible so it as to be as small as possible.
6.4. Exploit
The execution of the epxloit as to be very fast to be less noticeable as possible. This phase can be mitigate by the use of host level software like antivirus or anti-malware.
6.5. Installation
In this phase, the code written by the attacker will get the payload of the malware from external sourcel like internet or code embedded in some other non executable phases and then delete every trace of the execution. The presence of the payload as to be obfuscated as much as possible.
6.6. Callback
After the installation of the payload, the malware cleans up what remains of the installation procedure, then start a beaconing procedure, that consist in contacting a C2 server to receive further instruction, download modules and send identify information about the machine on which it is installed. Possibly it sends informations about basic characteristics of the local environment togheter with a unique key of its installation; the key can be formed by the hash of different parameters of the machine, the network name or the GUID provided by the Registry Key. The beacon is an unidirectional message from the malware to the C2 server, to let it know that it is ready to receive commands, it hapens periodically until the malware hears back from the C2 server; for this reason the beaconing activity has to be coded in such a way to be less noticeable:
- Sneak beaconing traffic along with non malicious traffic
- Hide the beacon inside other messages (using social networks, query DNS, use emails). Some malware have a procedures that create an hostmane composed with some informations and they query that hostmane that is register to a general domain, the server associated to that general domain will receive the query and so the beacon.
The interaction between the C2 and the payload is obviusly obfuscated, typically the communication protocol may include several diffirent commands that directly match the functionality of the malware itself. Oftenwhile the RATs in order to be less identifiable their first installation is light, but they can ask a C2 server the download of new modules. The communication is strongly asynchronous, via undirect channels.
An example is represented by donwloader.BMP.exe malware, that used steganography to encrypt commands in a BMP file header. Another more recent example is represented by the trojan.msil.berbomthum.aa that downloaded memes from a set of twitter profiles that included commands like: print clip and docs. The rate of communication using this kind of techniques is quite low, but in this phase it is not a problem.
6.7. Data Exfiltration
In this phase the communication rate matters, because the malware would transmit GBs of data; thats because any information in a single PC can be valuable: passwords, private encryption keys, documents, and network information. Most of the malware are spotted during this phase, because it is very suspicious to see gigabytes of data travelling from a local machine. From a defender perspective, it is very important to setup an anomaly detection tool in order to define all the allowed data transfer policies, to spot any suspicious data transfer. Of course also in this phase the malware will try to hide his activities; for example using a very slow transfer rate combined with file compression. The data transfer rate is decided also taking into account the level of network security of the target.
In this phase the motivation of the attack plays an important role, for example if the attack is targeted, the malware will act in such a way to retrieve the goal of the attack; otherwise it will try to extract anything of interest. Whatever the case may be, it is difficoult that the malware will be capable to access the final piece of information that it’slooking for at the first infection. For this reason the malware may want to gain administrator privileges, or monitor the surroinding network to infect a different trusted domain to move closer to its objective.
6.8. Lateral Spread
This stage arise a new iteration of the attack, and allows the attacker to move further to its goals, so the concatenation of several attack killchains compose the multi-level attack.
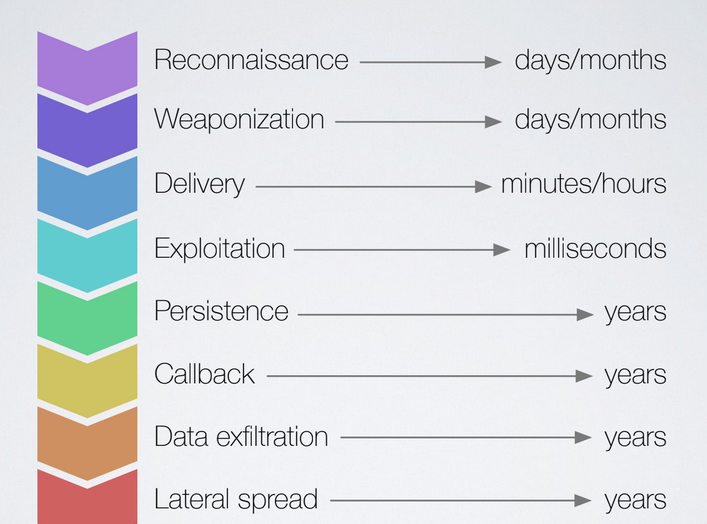
For each of those phases, appropriate contermeasures have to be used. For example during the explitation phase automatic tools have to be used, on the other hand during the callback phase a human analyst can spot communications between the malware and the C2 server by looking at the logs. From a defense perspective we want to stop the attack during the inital phases of the attack killchain, to know in advance the possible attack paths that the ataacker will use we have to use Threat Intelligence techniques.