Risk Management Methodologies Review
Table of Contents
1. Lecture 11
- Class: Security Governance
- Topic: Risk Management
Risk management methodologies provides a pragmatic framework that can be used to implement all the guidelines prvided by the standard. All the methodologies must be compliant to the different standards, The methodologies discussed here are indeed compliant with ISO 27001 and 27002, even if they do not cover the whole process but just a subset.
The three methodologies presented work at different levels of granularity.
2. OWASP
This methodology, is a structured list of steps that can be easily instanziated. It is based on the two factor risk model (explained here).
It also gives the possibility to customize the analysis.
2.1. Risk Identification
OWASP suggests to gather information that will enable the computation of the risk level based on the factors used by the methodology itself. The factors are four, and each of them depends on four different aspects.
First of all the method says to gather information about:
- the threat agent involved.
- The attack that will be used. So the concrete explotation used by the source toward the asset.
- The vulnerability.
- Impact of a successful exploit on the business. It is important to define the relationships between the ICT part and Business part of the organization.
The OWASP methodology does not provide any direction on how to identify the risk, so this process has to be performed by the assessor following other methodologies or references.
2.2. Factors for estimating likelihood
The likelihood estimation is based on two main relevant aspects. The first is the threat agent, and the set of vulnerabilities that are possible entry point for the specific attacker.
2.2.1. Threat Agent
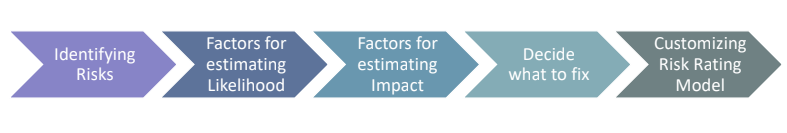
For a given threat agent four factors must be considered: skill level, motive, opportunity and size. Each factor pose one question to the analyst; for each answer must be assigned a score between 0 and 9. Of course the methodology gives some suggestion about reasonable value assignment, but it is up to the analyst to assign the correct value.
NOTE the skill level score has been inverted in the online tool.
The skill and the motivation are linked also to the kind of vulenrability considered, if the system is full of difficoult vulnerability to be exploited the motivation of the attacker plays an important role.
Regarding the size, we compare the possible size of the group of threat agents to the size of the developers or system administrators that really know how the system works, ranging to the anonymous internet user.
Higher is the score, higher is the probability that the threat source will attack the system. The score is given by the average of the score of the four factors; the score represent the likelihood of a given threat source.
2.2.2. Vulnerability
Then we have to analyze the vulnerabilityies that may lead to a possible successful exploit. Also in this case four factors must be considered, fixed a threat source; that’s because the score of a vulnerability depends on the threat source.

Considering awareness the MITRE CAPEC repository may be used. The score represent the dangerousness of the vulnerability given a fixed threat source.
2.3. Estimation of the impact
The impact could be estimated looking at two orthogonal perspectives: the ICT perspective and the Business one. The technical impact can we considered on the application, the data and the functions it provides. The business impact is related to the support that the application may give to the business functions of the company. Having low ICT impact does not necessary mean that the business impact may be low.
2.3.1. Technical Impact
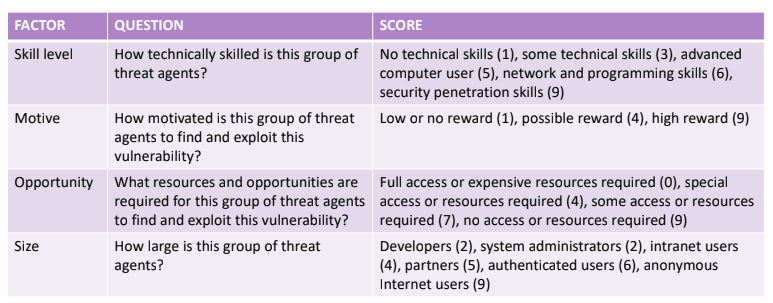
It can be estimated considering four factors: confidentiality, integrity, availability and accountability. The goal of this step is to estimate the magnitude of the impact on the system in case of the threat is materialized trough the exploit of the considered vulnerability.
The methodology gives directions, but the analysit has to customize it to the companys needs.
2.3.2. Business Impact
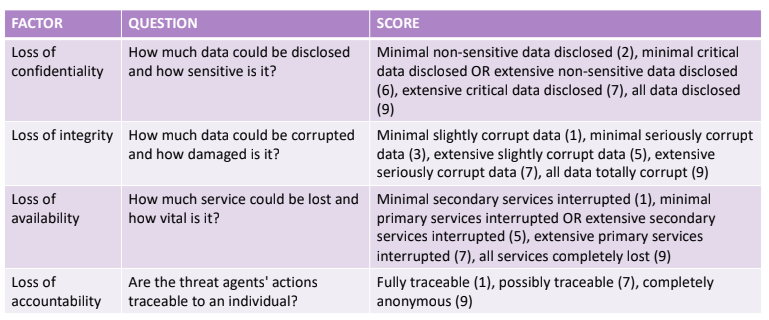
This dimension is very difficoult to be assessed; it is composed by four factors.
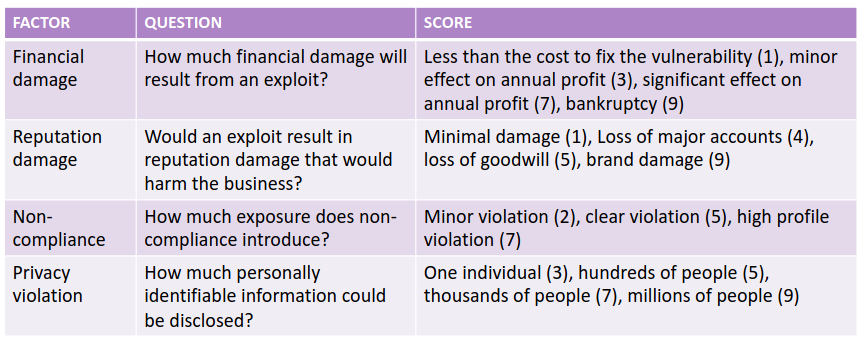
The collaboration with the accountant departement is needed to perform an efficient mapping between the ICT and the Business aspects of the company. The non-compliance aspect is a perfect example of how low ICT impact can represent an high business impact: considering GDPR a single record violated represent a complete non compliance to the regulation and the payement of an high fee.
2.4. Determing the severity of the Risk
Two arrpoach can be used: informal method or repeatable method. In the informal method the owerall risk level is represent by qualitative values, while with the repeatable method a more formal approach is used. A documentation that justify each decision is produced and the analysis is repeated during time to confirm or update it.
An example of informal method:
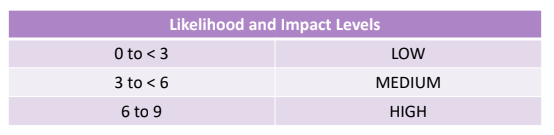
An example of repeatable method:
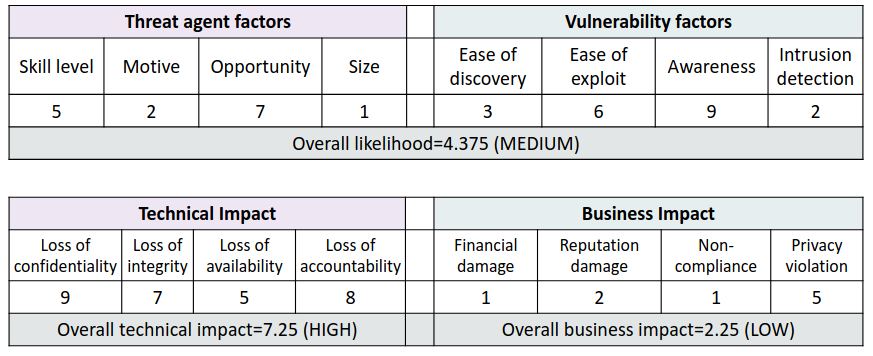
Once we have acquired the values the severity must be determined considering the likelihhod and the impact, the OWASP methodology also provide a observation:

In the end the risk is represented inside the risk matrix:
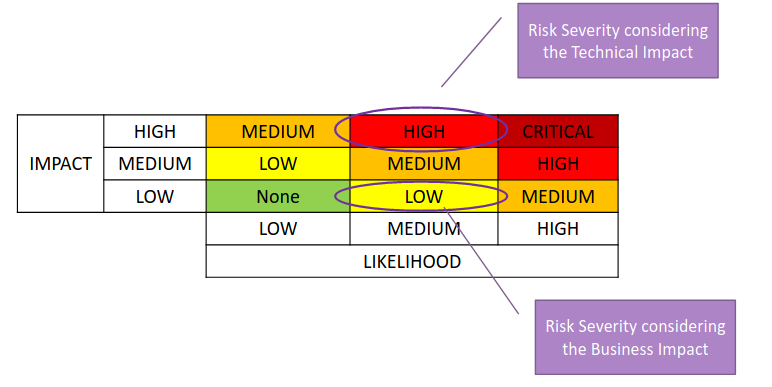
2.5. Deciding what to fix
After the risk to application have been classified there will be a prioritized list of what to fix. As a general rule the high priority will be assigned to the most severe risk, also not all risk are worth fixing, for example can happen that a fix may cost more than the occurence of the incident itself or that the risk has an huge impact but a very low likelihood and so it is shared but not fixed.
2.6. Customization
The customization part gives some information on how to customize the OWASP model to better tailor it for the organization. Some actions to put in place can be:
- Add new factors
- Customize options
- Assign a better score to the factors
The OWASP methodology is supported by an online tool.
2.7. Summary
| PRO | CONS |
|---|---|
| Structured in few simple steps | Allows only a course grained risk analysis. Complex situations are difficoult to analyze |
| Easy to apply | Does not provide too much support to the risk mitigation phase |
| Supported by open source tools |
3. CRAMM
The CRAMM methdology comes from the UK governement, but it is not publicly accessible and very few documents can be found on the web. There is a proprietary tool that support the methodology. It is a lightweight methdology and it focuses on how to gather data and how to use them to feed the tool. The real estimation is done automatically by the provided tool.
This methodology suggest to leverage on the human factor to collect the data via meetings, interviews and quastionnaires. The data is then organized in a structured format. It is composed by three phases:
- Indentifying and valuable assets
- Indentifying threats and vulnerabilities and calculating risks
- Identifying and prioritizing contermeasures
3.1. Identification and Valuation of Assets
In the first stage the methodology stress on the existence of three particular kinds of assets: data, application sowftware and physical assets. The aim is to enlarge the view on the context around the digital services and how they are provided.
3.2. Indetification of vulnerabilities and threats
Threats and vulnerabilities are investigated against selected asset groups, and the structural point is that CRAMM provides predefined tables form threat/asset group and threat/impact combinations. The tool is fed with the data collected and produce a managerial level risk assesment: it works an high level aggregating the types of threat and vulnerabilities.
3.3. Assessing Risks
The methodology provides two alternative way to assess risks: full and rapid.
| Full | Rapid |
|---|---|
| Threts and vulnerabilities analysis is driven by questionnaires allowing to entering the answer in the tool | threat and vulnerability levls are inputted directly with a rating guide |
| Use the tool to calculate levels of threat to assets as well as levels of vulnerability to threats |
3.4. Indentify and prioritize countermeasures
Via the toll CRAMM roduces a set of countermeasures applicable to the system, it works on the detail of the mitigation. It does it by reasoning on the security profile and compare the mitigation with the target security profile and plan how to implement the mitigation. CRAMM supports also the prioritization of the mitigation techniques provided. It takes into account if:
- it protects against several threats
- it is required to protect a high risk system
- there are no alternative countermeasures installed
- it is less expensive to implement
- it is more effective to meet the objectives
- it prevents an incident instead of facilitate recovery.
3.5. Summary
| PRO | CONS |
|---|---|
| Structured in few simple steps | It can be only applied via a proprietary tool |
| Oriented to the management |
4. MEHARI
MEHARI stands for *ME*thod for *H*armonized *A*nalysis of *R*isk, is a free, open-source information risk analysis assesment and risk management method, for the use of information security professionals. It is designed to be compliant with ISO 27005 and ISO 27001.
There is no automatic tool that implement the MAHARI methodology, as to today the most advanced tool is a macro powered excel file.
The MAHARI methodology is organized in three macro-blocks, each one is composed by different sub-activities:
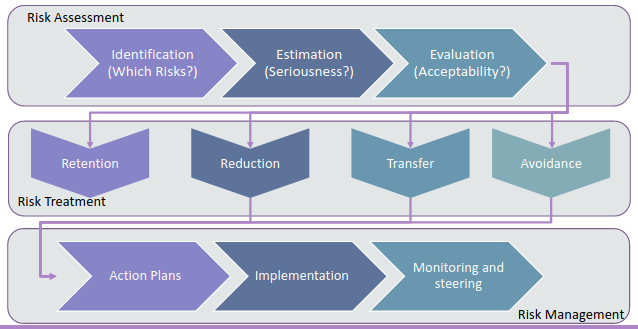
Note that the component of the first macro block are exactly the first three activities inside the ISO standard. The risk treatment block also is mapped 1 to 1 to the ISO standard.
4.1. Identify Risks
To identify the risk there are two question to answer:
- What is the best way to do this?
- characteristic elements of risks must be highlighted but how many details must be described?
The first thing to do is to identify the assets, analyze their vulnerabilities and then look at the threat:
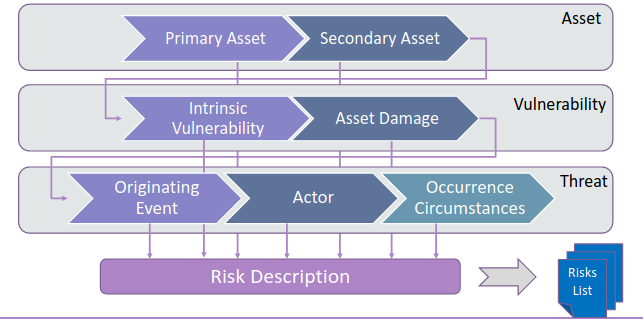
4.1.1. Assets
4.1.1.1. Primary Assets
A primary asset is an asset that can be described using the followng table:
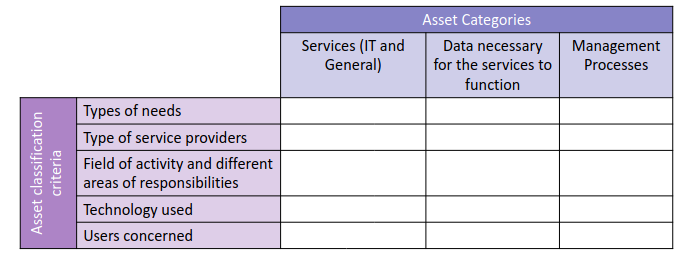
the instructions on how to fill up the table is provided in the Appendix A1. They are related to the business aspect of the company, in general we can say that a primary asset is an asset that represent a value for the company.
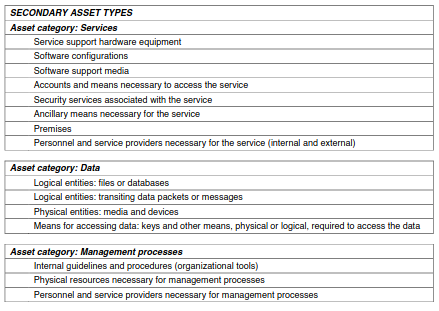
4.1.1.2. Secondary Assets
They are those assets that do not represent directly a value for the company but they’re needed to support a primary asset. A naive example is: for any company a primary asset is network connectivity, it depends on the availability of routers and swithces that are secondary assets.
Also in this case a table is provided in the Appendix:
4.1.2. Vulnerability
Also in this case the repository contains tables full of high level vulnerabilities that can be considered.
4.1.2.1. Intrisec Vulnerability
It is an intrisic feature of the system prone to a specific threat.
4.1.2.2. Contextual Vulnerability
The contextual vulenrablity is somehow what is needed in the environment to enable the vulnerability. For example an OS has a vulnerability that can be exploited if and only if a specific application is installed.
4.1.3. Threats
The MAHARI model then provides a way to identify the threats.
4.1.3.1. Originating Events
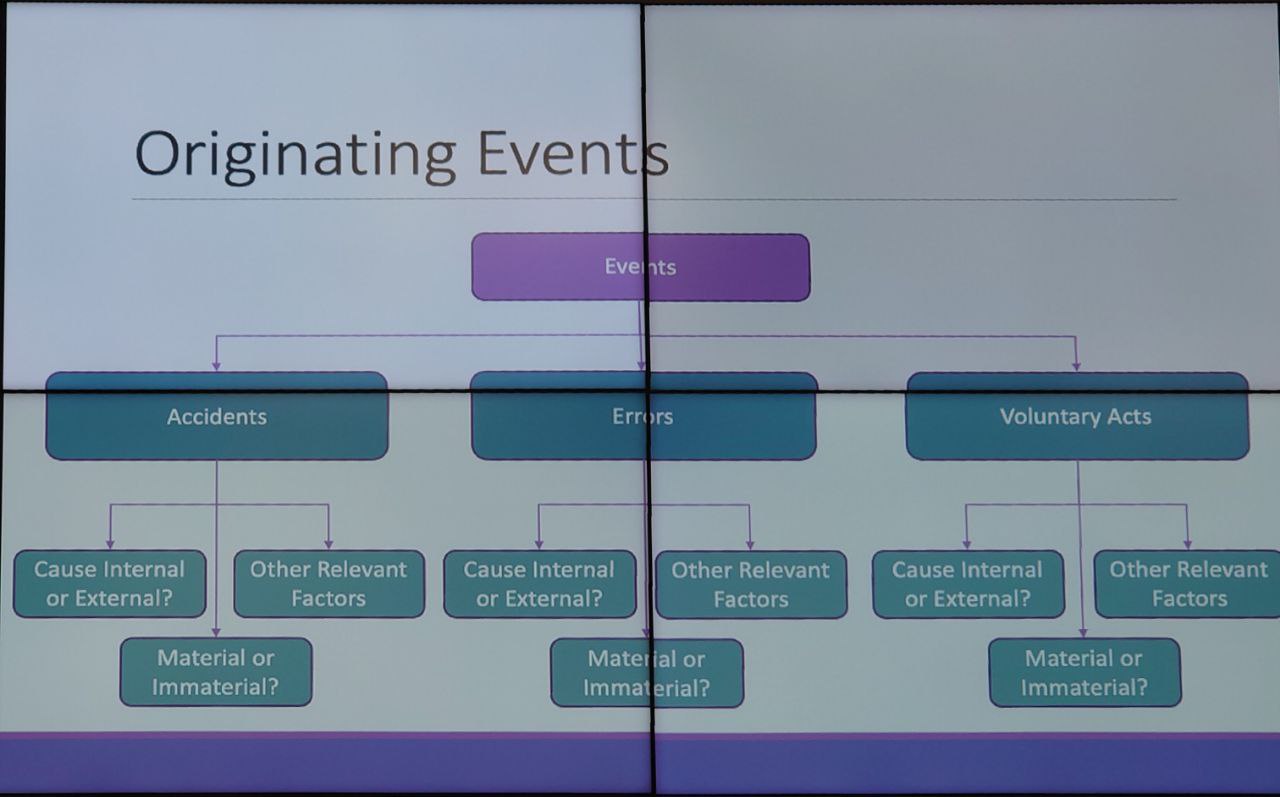
4.1.3.2. Actor
Once the originating events are evaluated the actors can be considered. If the originating point may be a person we have to consider the rights that the person has over the system and how he can interact with it (for example if he/she has access to an account with privileges or if he/she can access to restricted physical locations). Of course not all the actors have the same capabilities, so the right actor has to be associated with the right originating event. Also in this case a table is provided.
4.1.4. Summary of Risk Indentification
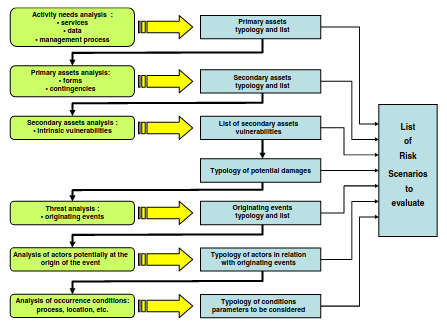
4.2. Estimating Risks
The risk estimation is done via the common two factor model, in this methodology is important the distinction between the intrinsic impact and the instrinsic likelihood, then the effect of security measures on these two parameter are considered. It is like to go from the worst factor and then adjust it considering all the policies, prevention, and detection measures.
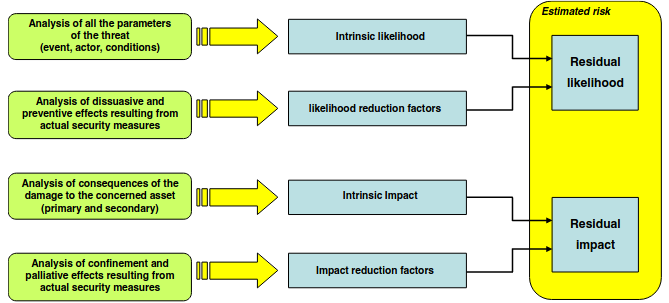
4.3. Evaluating Risks
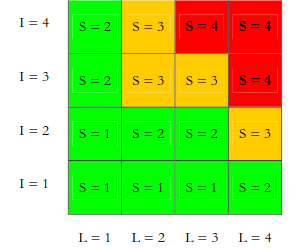
The evaluation step is done by placing the risk in the risk matrix. MEHARI provide the matrix and categorize the risk into three levels: intolerable, inadmissible and accepted.
4.4. Risk Tratment
It refrase what is exaplained is the ISO standards, it do not support the analist with prioritization.
4.5. Risk Management
It simply repeats the general principles discussed in the standards without providing any addition nor support.