National Framework for Cybersecurity and Data Proteciton
Table of Contents
1. Seminar on the “National Framework for Cybersecurity and Data Proteciton”
- Class: Security Governance
- Topic: National Cyber Security Framework
- By: Marco Angelini
2. Framework Nazionale
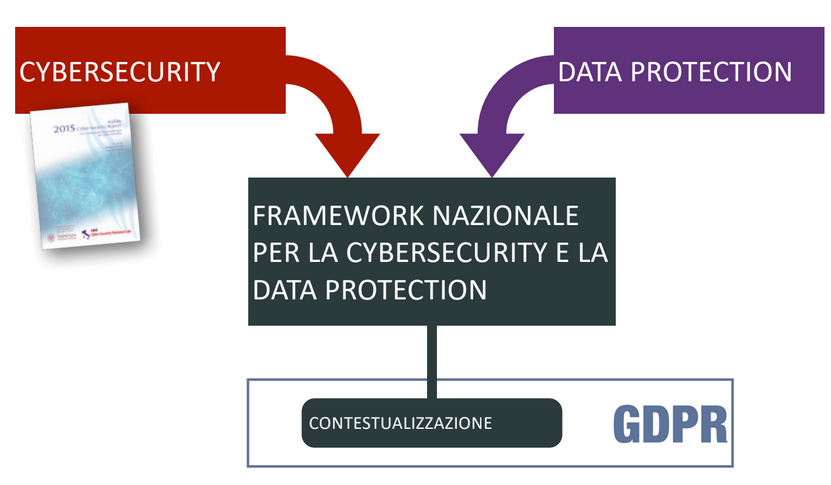
In the 2015 there was the first edition of the National Italian Framework, it is based strnctly on the NIST framework, with the difference that it was not reserved only to the Critical Infrastructure. In 2016 there was and addition that extracted the essential controls for cybersecurity, a document done to support also small realities, to at least produce awareness and inform a more general public. In 2018 the National Framework for Cybersecurity and Data Protection was published, it is the current standard and introduce some contents that are helpuful to produce a good contextualization.
From the 2022 the National Framework is fully integrated inside the Italian Perimeter, and strongly encouraged for PA, Enterprises and PMI; it is fully recognized in Italy. For integrated we intend that all the members of the “perimeter” must implement the National Framework.
The next step is to contextualize it for the Health Care sector.
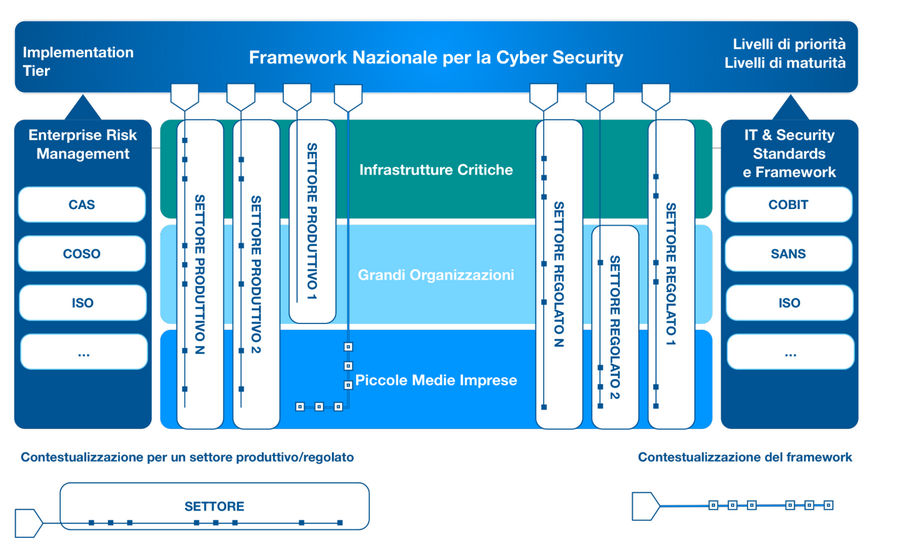
3. Structure
The bas structure of the National Framework comes from the NIST Framework, starting from the core the first big difference is represented by the levels of security, but the main difference is the concept of contextualization.
3.1. Contextualization
In principle it is a cut of the core, that can be defined from de most basic organization to the most complex. The framework can be adapted to a specific scenario using contextualization; to create a context different steps are needed:
- Selection of subcategories. some sub-categories will be selected other will be not considered.
- Priority Levels. The second step is the definition of the priority level for each selected subcategory; this is not a total order of execution, but it gives additional information:
- High. Fundamental sub-category to implement, without considering cost, maybe it is mandatory by law
- Medium. To be implemented considering cost-benefit trade-off
- Low. Maybe is more costly than effective, so the implementation of a Low priority sub-category …
- Maturity Levels. It does not express anything about the coverage, but it express the status of maturity of each sub-category implementation. For each maturity level are provided the test to check if the selected level of maturity is correctly implemented.
Given a Contextualization it is possible to obtain the Current profile as is, so the current situation of the organization; then it is possible to define the ideal profile, so the target profile. The target profile can be decided in terms of reasonability and legislation, and can be incremettaly redefined. Of course using the current state and the target one is possible to conduct gap analysis. It can be done for a single organization, a group or an entire sector.
3.2. Methodology
- Identify or Define a contextualization
- Define priority and context
- Identify systems and assets (end of contextualization)
- Indentify the current profile
- Conduct risk analysis
- Identify Target Profile
3.3. Context - PMI
It consist of 93 subcategories out of the 98, with three priority levels and three maturity levels. This contextualization is already provided by the document, so a PMI can start from point 5 of the Methodology.
3.4. Drawbacks of the first version
The most important one was that the framework didn’t covered at all data protection activities (1 to 1 mapping to the NIST framework, that it not covers Data Protection activities). The second important aspect was that it was very difficoult to add new references to include new regulations or domain specific documents, for example the finacial sector regulations. The third drawbacks was that the self creation of the contextualization would create a very heterogeneous situation, with hard to compare implementation of the framework.
4. Framework Nazionale 2.0
Today the National Framework core is a superset of the NIST Framework’s core; that means that it extends the NIST core with additional sub-categories, not necessarly limited to the GDPR but related to it. Then it was created another sematinc element: contextualization prototype that is propedeutical and can be used to create a contextualization in a more methodologic way.
4.1. Update to version 1.1 of NIST Framework
It was added one category related to the supply chain, and 10 subcategories.
4.2. Framework 2.0 Core
There were added diffrent informative references: GDPR, G.Lgs. 65/2018 and AgID. Then in the core were added element that regards Data Protection, the added cetegory and subcategory govern all the aspect of the data lifecycle, including their international transfer and how to respond to the communciation of a data breach.
4.3. Contextualization
It is not easy to contextualize the framework to a particular domain, a strong domain expertise is required, there is a lot of freedon in defing the elements and an absence of a guided process; furthermore the contextualization process does not produce intermediate results. This lead to the creation of the Contextualization prototypes.
5. Contextualization Prototypes
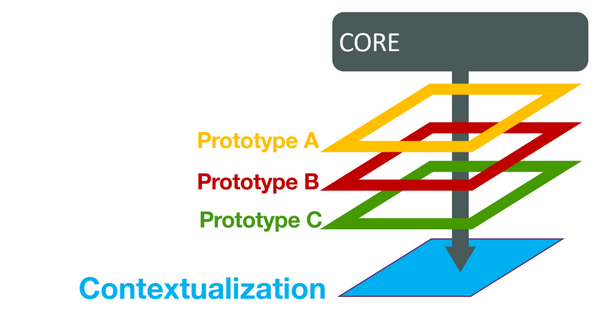
A contextualization is not capable to capture a single law/regulation, standard or best practice, a divide et impera approach has been applied to produce the contextualization prototypes. They are a new instrument to define contextualization templates, it can be created once and reused everytime a context require the inclusion of specific regulation, technical standards or best practices, shrinking the expertise required to produce a contextualization.
Given a reference that we want to map, for each subcategory of the Framework core must define its class: mandatory, recommended, free (means that nothing is said for that sub-category on the mapped reference), eventually a priority level may be defined. The priority scale may be defined as before (high, medium, low) or may be defined as defined on the informative reference model.
Then a document that accompany the contextualization prototype contains the application context, additional contraint on the selection of sub-categories, the definition of piority levels and a list of security checks, each of the considered sub-categories will be positioned in several maturity levels. At the end of these steps a protoype is created: it is not a contextualization, the latter may be made of different prototypes treated as as layers.
5.1. Implementation of a prototype into a contextualization
All the mandatory subcategories in the prototype are included in the contextualization, where the inclusion of the recommended must be evaluated, considering elements coming from the application context (for example in GDPR the context is very broad). Eventual additional contraints regarding the selection of sub-categories, and described in the implementation guide. The second steps regard the prioritizaiton of each of the selected subcategory, it should be at least or equal or more strict than the one defined in the proptotype. All the security checks can be integrated in the implementation guide, fitting them on the whole contextualization.
When considering differnet prototypes some problems may arise, for example if two different prototypes have some level of intersection. Considering priorities, if it at least one the priority level is high, the final priority of that level must be high, but it is not the only reasonably choice, consdering a cost based approach the minimun priority level between the two can be applied.
Considering Maturity Levels and Security Checks, normally the Maturity Levels are choosen based on the prototype that has the more levels, if a security check of a prototype clash with the security check of another the intervent of an expert of the domanin is needed. The security checks are not limited to technical aspects, but also to procedures and processes.