Introduction to Risk Management
Table of Contents
1. Lecture 6
- Class: Security Governance
- Topic: Risk Management
2. Risk
Informally a risk is the potential that something goes wrong, so it has to be taken into account because when it happens it will create troubles.
A risk is the likelihood of an incident and its consequence for an assets.
- Asset. An asset in anything that represent a value for a party. It could be something concrete (like equipment or machines), or something abstract (like data, reputation, information). When discussing about cyber risk, one of the assets that are taken into account is the reputation. When the risk management is carried out it is possible to consider not the whole organization but a part of it, like a stakeholder, a group of people or machine; in general it can be a subset of the whole organization. That is because different parties can have different needs and assets related to their scope.
- Likelihood. It is the chance of something to occur, so the chance that something happens. It is an abstraction of the mathematical concept, the definition is vague on purpose. The likelihood will always be related to an incident.
- Incident. An incident is an event that harms or reduces the value of an assets. It has to be identified first, and then it is possible to compute the likelihood that the incident happens.
- Consequence. The consequence is the impact of an incident on an asset in terms of harm or reduced value. It is fundamental to finally quantify the level of risk.
All this set of activities are included in the risk management process. We are defining a process composed of coordinated activities with the aim of direct and control the risk metrics:
- direct part: create directives to reduce the risk
- control part: measure and quantify the level of mitigation produced by the direct part
2.1. Requirements
A risk management process must be adequate, efficient and effective. Adequate means that the risk management process must be cost - benefit effective; Efficient means that the evolution of the process must use the really needed things in the most efficient way, governance processes can be quite rigid to be implemented, if they are not efficient they will cause additional expenses; Effective means that the outcome of the risk management has to produce some benefit that really support the direct control loop, in such a way to increase the well-being of the company.
2.2. Construction of a Risk management Process
The first thing to do is trying to setup the operative framework that will assist the company in the implementation and design of the process. The framework is built on the principles contained in different standards.
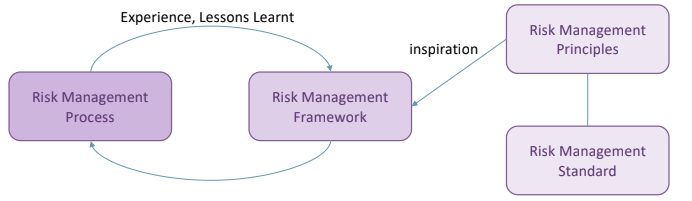
Starting from a standard, that is chosen in accordance with the context, then after principles are selected the framework is built implementing the risk management process. After putting in place the process it must be observed to check if it is adequate, efficient and effective; and possibly fix it via continuous improvements.
3. ISO 31000
It is a standard for risk management, it gives general guidelines used to build a risk management process. It provides direction on how to structure the process without giving instructions on a specific sector.
The information provided support the risk management in the whole lifecycle of the company, and across all the phases of the risk management process. It can be used to compare approaches used by different companies, but it can be used to acquire a certification. So it can be used as an internationally recognized benchmark to compare risk management practices between organizations.
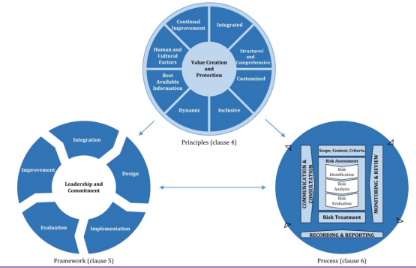
3.1. Principles
The core element is the main principle to keep in mind when defining the process: Value Creation and Protection. It suggest that the value protection has to consider the business aspect of the company and manage the risk consistently accordingly.
3.1.1. Integrated.
It explain the fact that the risk management process should live together with the other parts of the company. So it should be pervasive in order to protect properly the assets increasing the value of them.
3.1.2. Structured and Comprehensive
It should be not made like an improvisation, but it has to be at least conceptually structured, so to know the purpose of each activity and the role of each actor. Comprehensive means that the risk management process must take into account the whole reality of the organization.
3.1.3. Customized
Each company is different, and has different internal structure and processes. So the risk management process has to be customized to be efficient and effective. The customization should be done also looking to the external context, like dependencies, partners and providers.
3.1.4. Inclusive
The process must involve all the people that are interested, and may benefit from the result of the analysis. That’s important because most incident comes from lack of awareness.
3.1.5. Dynamic
In the context of cyber the world changes very rapidly, so the process can’t be static but it has to evolve during time.
3.1.6. Best available information
The information used have to be of high quality, that can confirm the analysis, provide multiple perspective and tell more about the incident. So they must be timely, clear and available. Sometimes having a lot of low quality information is worse than having less high quality one. The information gathering has to be continuous to ensure the improvement of the process. Ideally the information gained should be validated.
3.1.7. Human and Cultural Factors
Behind the risk management process there are people, so it is possible that the assessment produced can be influenced be their opinion and interpretation of the data. It is not a problem that can be solve in a deterministic way, because there is always a subjectivity point.
3.1.8. Continual improvement
The risk management process is not static, it has to improve during time reacting to changes and correcting possibly misbehavior.
3.2. Framework
The framework is based on the principles, the framework is used to drive the implementation of the process. It’s purpose is to assist the organization in the integration the risk management processes in the business activities. The second objective is to guarantee the effectiveness of the process considering the cost - benefit trade off, tuning the integration in the business flow of the company.
The central component is Leadership and Commitment, there should be a person or a group of people that has to be fully committed to the risk management activities (notion of role and responsibilities).
3.2.1. Design
Design of the process itself, which activities and how they should flow during time.
3.2.2. Implementation
Move from theory to practice
3.2.3. Evaluation
Evaluate the process to improve it.
3.2.4. Improvement
After the evacuation of the process improvements are designed.
3.2.5. Integration
Integrate the improvements.
The hard part of the implementation is the customization on the process to be adapted to the company.
3.3. Process
Set of processes to implement inside the set of activities that compose the risk management. The central process regards how identify, analyze and evaluate the risk; the other processes used to support the central one.
3.3.1. Risk Treatment
3.3.2. Communication and Consultation
Is the set of process composed of all the action performed to communicate the outcome of the analysis to increase the level of awareness. The communication should be done in a structured way, so identify the procedures on how to collect data and how to communicate them from and for the process. The communication process should support all the actions of the risk management process.
3.3.3. Monitoring and review
It is the set of activities aimed to improve the quality of the process. So observe, get and interpret data acquired from the process and use them to improve the process itself. Also this part has to monitor and review every part of the process.
3.3.4. Recordind and Reporting
It is a good practice that helps the company to take snapshots of the risk management process. It can be considered like a log mechanism used to create historical data and support during the analysis.
These four aspects have to work together to guarantee and adequate, effective and efficient process.
4. Risk Management General Process
The risk management it is composed by 3 main sub-component, the recorded and reporting part is very customizable, so there are not particular definition and suggestions. The 3 main sub-components are tightly related one to the other. The monitoring and risk assessment part are supported by a good communication and consultation, at the same time the risk assessment can be improved via a good monitoring and review process. The less obvious relation is the one between communication and consultation and monitoring and review; the relation enable a better understanding of the nature of the problems.
4.1. Communication and Consultation
This subprocess is composed by four main task:
- Establish a consultive team. It is needed in order to gather information to different points of view. When building the team it is important to include all the possible expertise and information sources needed to gather the information. Identifying the relevant stakeholder, contributors and who will benefit from the information collected. You may also involve external entities that helps identifying common threats in the particular domain of the company, considering the cyber part this last part is particularly important (for example collaboring to a SOC). It is important to clarify the role and responsibility of each member of the team, in such a way to produce an effective outcome, identifying responsibilities in case of issues (fatcors related to efficiency).
- Define a Plan for Communication and Consultation. In this case the team should decide which are the procedures to follow in order to gather the input needed for the analysis and how to share the outcome of it; mapping also who and how contact each actor. The stakeholders have to be contacted only when they are really useful. When gathering input the team has to consider information that are appropriate and consistent to the risk evaluation criteria, so the team has to be aware of the risk assessment procedure to ask the information in the right way. Of course whose taking decisions (strategic level) has to be informed of the outcome of the team: result delivery.
- Ensure endorsement of the risk management process. The team has to have full support of the management, to ensure collaboration between the team itself and other parts of the company; at the same time there should be common agreement and mutual understanding of how the risk should be managed.
- Communicate Risk Assessment Results. The result of the assessment are important in all the level of the company. On the strategic level it is used to decide on investments, actions or corrections. On the operational level, being aware of the risk will result on the correction of bad behaviors that can be improved just via awareness, spreading the result of the risk analysis; creating a common level of knowledge of the risk. Efficient communication is fundamental in all the level of the stack, the means of communication are important, for example if a policy restrict the actions of the employees will create a low level of collaboration from them; for this reason the communication strategy is fundamental. It is important to communicate the results to external parties, keeping into account trust.
4.2. Risk Assessment
The risk assessment subprocess is made of five main steps. The steps can be performed in a sequential and iterative way, but it is also possible to rollback from a step to another before going forward to get new data and additional information to reduce the level of uncertainty or for assess the level of completeness.
4.2.1. Context establishment.
It is the first activity, it consists of the identification of the context relevant for the assessment considering internal and external factors. Internal factors take into account internal standards, policies and procedures, where external factors are represented by law and regulations. The outcome is composed by different parts: the target of assessment, then the boundaries are refined considering the perimeter of the analysis to be performed. The focus is the main issue or central area of attention in a risk assessment. it is important to keep track of the assumption taken during each step. Assumptions are taken for granted or accepted as true about the system in question. At the end of the task the outcome is the formalization of the context, that is a document that contains who is the client (people that asked to perform the assessment), the assumptions taken, the relevant assets that will be analyzed and the scale used to measure the risk, so how the risk value is evaluated and how to measure consequences and likelihood.
4.2.2. Risk identification.
The risk identification is the set of activities aiming to identify, describe, and document risks and possible causes of risk.
In this phase We have to identify all the possible causes of a incident, and the way in which the incident may became concrete. Some observation are taken into account:
- A risk is always associated with an incident.
- There are three elements without which there can be no risk: assets, vulnerability and threat. To an incident to became true there are to be present all of three components.

The scope is to identify, starting from the assets, all the possible incidents that have associated some real threats and vulnerabilities; establishing the likelihood. A risk is present if there is a vulnerability in the system, a threat source and a threat.
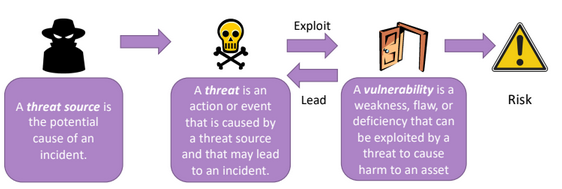
Considering the cyber world, the presence of a vulnerability inside a system can lead to a domino effect.
4.2.3. Risk Analysis.
The risk analysis is the activity aiming to estimate and determine the level of the identified risks.
The number associated with the risk is a function of the likelihood and the consequences of it. So to estimate a risk we have to estimate its likelihood and consequences.
4.2.3.1. Likelihoods Estimation
After that we have fixed the context of the analysis, We compute the probability that the incident happens, to do that we need to collect data from the environment, a lot of aspects must be considered.
Statistical analysis tools are used to infer the likelihood. Sometimes the data is not enough or not appropriate to be used during this sub-phase. There are some guidelines that can be used but human expertise is needed to adjust the results.
4.2.3.2. Consequences Estimation
The dependency and the contexts have to be taken into account together with the asset. It is not so easy to estimate the consequences of an incident; so this process should be conducted by a walk-through of all identified incidents and assigning the estimates with the involvement of personnel that can judge the consequences on behalf of the party.
4.2.4. Risk Evaluation.
The risk evaluation is the set of activities involving the comparison of the risk analysis results with the risk evaluation criteria to determine which risks should be considered for treatment.
in this phase, all the risks identified are considered as a whole, to check if there are some correction to perform. It is composed by four activities.
- Consolidation. Evaluate how much the estimation of the risk is impacted by uncertainty; theoretically We want a 0 level of doubt, but in reality it is impossible because statistical tools are used in the identification phase. Of course if the error is low the overall impact will be low; if it high it might be needed to perform additional analysis to reduce it at an acceptable level.
- Evaluate the risk level. Look where the risk is placed in the risk matrix, to make a prioritization.
- Risk aggregation. We’ll see the single risks can be aggregated to consider a general one, where few individual risks that stay in the green part but taken together or in sequence can be considered as red. Another criteria of aggregation can be to look on different incidents that can impact a single asset.
- Risk grouping. Risk can be grouped if they have common elements, like if they are caused by the same set of vulnerabilities.
4.2.5. Risk Treatment.
The risk treatment is the set of activities aiming to identify and select means for risk mitigation and reduction.
This is the last step of the assessment process. Ideally we would manage each risk in the matrix, but practically it is not possible, because there are monetary, time and other constraints. In summary resolving a risk can be less affordable than accepting it.
There are four main options for risk treatment.
- Risk Reduction. It is the most common option to apply, it consist on trying to find which are the elements to be put in place to reduce the likelihood or the impact.
- Risk Retention. It is applied when solving the risk is more costly than accepting it; or when the risk has little likelihood and low impact or the impact is not critical.
- Risk Avoidance. In this case there is so active acting on the assets, but policies are put in place to be sure that the risk can’t arise in the first place, like a defensive barrier around the asset; acting on the root cause of the threat.
- Risk Sharing. This option consist on transferring part of the consequences to another party, like an insurance company or a sub-contract. This option is adopted in case of black swan: incidents with huge impact but little likelihood.
4.3. Monitoring and Review
It is composed by two main activities.
Monitoring is the continual checking, supervising, critically observing or determining the current status in order to identify deviations from the required or expected status.
The review activity is to determine the suitability, adequacy, and effectiveness of the risk management process and framework, as well as risks and treatments.
The monitoring and review part apply to the risk management framework, and of course to the underlying process. The main purposes of this process are to support the direct control loop by controlling the effectiveness of the process, and obtaining further information to improve the risk assessment; including in the process lessons learned in the past. At the same time it is used to detect changed, that van be huge between different iteration (update on the software, new machines, completely different set of vulnerabilities) identifying emerging risks. Stressing the fact that risks are not static, the risks can vary for different reasons:
- The assets can change in the value or priority, or because internal or external context (like laws and regulations)
- Vulnerabilities
- Changes in the context can lead to a change of threats, so every change may generate a review of all the risks.
This is the key elements for supporting the direct control loop. It is fundamental to monitor:
- Legal and environmental context
- Competition context
- Assets and assets value
- Risk evaluation criteria
- Resources required for adhering to the risk management framework