Cyber-Security Frameworks and Best Practices
Table of Contents
1. Lecture 4 and 5
- Class: Security Governance
- Topic: Cyber-Security Frameworks and Best Practices
- References: NIST SP 800-53, NIST CSF, Framework Nazionale per la Cybersicurezza
2. NIST
The NIST is the outcome of the Cybersecurity Enhancement Act that works in the Strategical and Tactical levels. It puts the focus in the fact that modern wars will be fought also in the cyberspace, so thanks to the CEA there was a simplification, but a generalization of the previous frameworks, that should try to develop a prioritized, flexible, repeatable and performance-based approach. The NIST has identified:
a prioritized, flexible, repeatable, performance- based, and cost-effective approach, including information security measures and controls that may be voluntarily adopted by owners and operators of critical infrastructure to help them identify, assess, and manage cyber risks
The fact that NIST was responsible to produce this new framework has lead to the NIST CSF: NIST CyberSecurity Framework.
The framework focuses mainly on the principal enabler of cybersecurity, giving support to the organization, it is made of three main components:
- Core
- Implementation Tiers
- Profiles
Each part is useful in each kind of company.
2.0.1. Applicability
The first thing that that consider was to provide guidelines to improve the cybersecurity if correctly implemenented. So it is not a framework indented to perform risk analysis, but it is an high level framework that tries to remain general to be used by many companies as possible.
It’s scope was to link together all the previous knowledge of the field providing a base common framework.
The initial target audience was mainly the critical infrastructure sector, that has particular challenges to solve. In a second moment they expanded the concepts expressed in the framework by letting it be useful for a wide range of companies that deals with:
- Information Technologies
- Industrial control systems
- Cyber-Physical Systems; especially in the second revision that consider also Connected Networks and IoT devices.
- IoT.
2.0.2. Features
The main feature it that the framework is technology neutral, so it do not consider any hardware platform, or particular technology to be as flexible as possible and effective during time.
The second important feature is that it tries to provide a link between all the existing concepts addressed in previous standards.
At the same time it provides a common taxonomy used to characterize the security posture of other organizations (in case of partnerships and acquisitions).
It can be used also to describe a possible state of the security level that the company wants to achieve, this is possible because the framework provides the instruments to plan a future objective and see how far it is.
Thanks to those instruments it can be also used to prioritize and rank the opportunities that can be used to improve in a replicable way in different iterations of the direct control loop comparing the improvements also between different companies, for example in a federated environment.
At last, but not least, it provides a common language that can be used for the communication between stakeholders.
So in summary the NIST CSF supports both cyber security assessment, and planning and monitoring activities.
2.0.3. Risk Management and CSF
It order to manage risks there is the need to identify the likelihood and the impact of the risks, the CSF helps to identify the set of risks to try to estimate the likelihood and impact of it; but the CSF can’t be used to estimate and quantify the risk.
2.1. NIST CSF Core
The core part of the framework is composed by a table composed by five security functions divided in categories, sub-categories and list of references to the different standards. The Core is not a checklist, it is a framework that gives a set of possible actions, not all of them may be important for some companies.

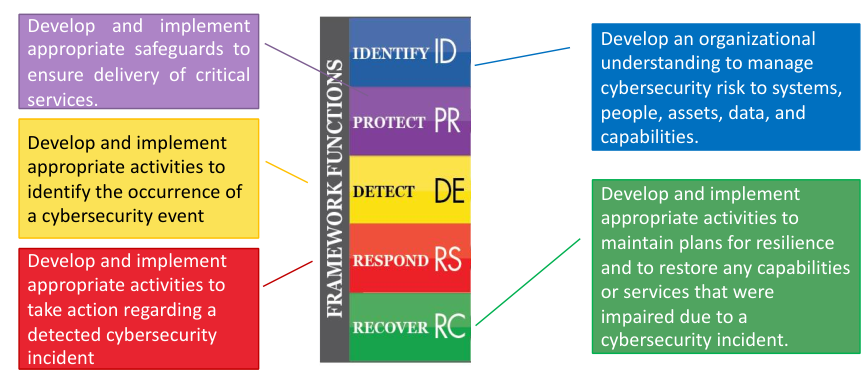
The categories are particular elements to be take into account for each category, where the sub-categories are refinement of each category.
2.1.1. Identify
There are all the control that are useful for identifying which are the important assets of an organization (starting point of risk analysis): people, data, IT infrastructure and similar. Also capabilities are considered assets, even if our focus is in the cyber domain is important to consider what is around the IT infrastructure.
2.1.2. Protect
Gives guidelines used to develop and implement activities used to ensure the delivery of critical services obstructing a possible attacker.
2.1.3. Detect
2.1.4. Respond
The response has to be as fast a possible, to try to contain the effects of an attack.
2.1.5. Recover
After an attack the company has to rollback to the state before the happening of the attack plus a mitigation strategy to be sure that the same attack can’t happen anymore.
2.1.6. Other elements
2.2. Implementation Tiers
The second part of the frameworks regard the implementation tiers. When the core tries to focus on the life cycle of the protection cycle, here the focus is more on the analysis of the implementation of the activities.
The implementation tiers ranges from Tier 1 (Partial) to Tier 4 (Adaptive), describing an increasing degree of rigor and sophistication in cybersecurity risk management practices.
They must be not used to represent maturity level of a company, for example a more flexible implementation can be more secure that a very strict one. Progression to higher tiers is encouraged when a cost-benefit analysis indicates a feasible and cost effective reduction of cybersecurity risks. They give to the management the right instrument used to know how and when increasing the tiers.
The tier is characterized by three elements:
- Risk Management Process. How you identify, and manage the risk
- Integrated Risk Management Program. How much the risk is considered in an integrated analysis with all the other elements of the company
- External Participation.
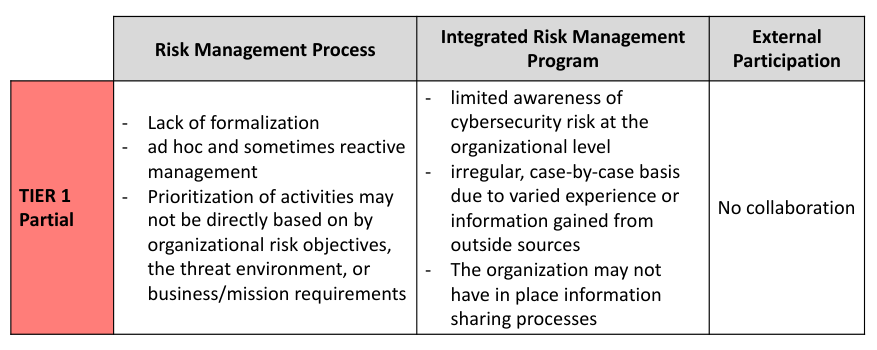
In the tier 2 there is the minimum amount of structure, with the fact that the management has a basic idea of the risk and how it can affect the company, with a first prioritization of the activities based on the risks.
The main differences between Tier 3 and 4 is the degree in collaboration and in the degree of precision and applicability of the standards and best practices.
2.3. Framework Profiles
They are filters that can be applied on the core part of the frameworks, abstracting the situation to consider, giving the possibility to identify a current state or a future state used to align Functions Categories and Subcategories with the business requirements, risk tolerance and resources. The NIST CSF do not share examples and template of profiles. This is one of the main problems of the NIST CSF, that has been addressed by the Italian Framework.
2.4. How to use it
- It can be used to identify opportunities for new or revised informative references, it is easy to identify the updates of the framework itself. At the same time it is easy to check for references changes that can lead to an update of the framework by mapping different framework stimulating improvements
- It can be used to strongly preserve privacy and civil liberty. It is possible to share which area of the core part are covered without revealing how.
- It also can be used for self assessment purposes by consider the sub-categories.
3. National Cybersecurity Framework
One of the main limitation of the NIST framework is the fact that it does not provide any profile that helps with the construction of the corporate ISM. The National Cybersecurity Framework is a derivation of the NIST, it is currently at version 2.0.
The work on the NCF started at the end of 2013 in Sapienza. It’s purpose was to provide a national context in Cybersecurity in a way that was simply for the medium and small enterprises; it is the result of a discussion between different research groups of Italy. The framework has the objective to be simple to understand, apply and cheap to be used by small and medium enterprises that are the majority in Italy; the starting point was the NIST because it is quite flexible.
The National Cybersecurity Framework has been developed in such a way to be also used outside from italy and be international recognized by other countries. First of all the NCF was intended to improve the information sharing capacity between parties increasing the level of awareness; at the same time they want something that was standardized at national level, to measure the capabilities of each company.
In the first version of the framework one of the key points was to present the idea behind the framework to public representatives to customize the NIST to the italian context and bringing improvements to the NIST framework:
- Measure maturity of the implementation of sub-categories
- Providing profiles
The first version was contextualized to the Public Administration offices: municipalities, ASL, offices. The first thing they did was running a survey to have a baseline of the state of awareness in cybersecurity.
The National Framework is not a standard (it is a de facto standard), so it is not certifiable. It is only a tool for self assessment, but in future it could became an instrument for certification. It allows organizations to assess their current cybersecurity posture (current profile) and define the desired one. That’s because in italy is difficult and not reliable for medium and small enterprises to be certified ISO 27001. so it is a good idea to provide directions and suggestions in a less rigid way. The final benefit of the framework is giving a roadmap to close the gap between the current profile and the target profile.
Given the fact that the NCF is derived from the NIST framework it maintains the same general structure.
3.1. Framework Core
There are the same five functions of the NIST framework, and the concept of Category and Sub-Category has been maintained, the Priority Levels have been added, preserving the Informative References and Guidelines are been added.
The first contextualization done regarded the Public Administration. The level of priority defined for P.A. are four:
- High.
- Medium.
- Low.
- Not Selected. It is a not critical element of the domain so it can be not considered.
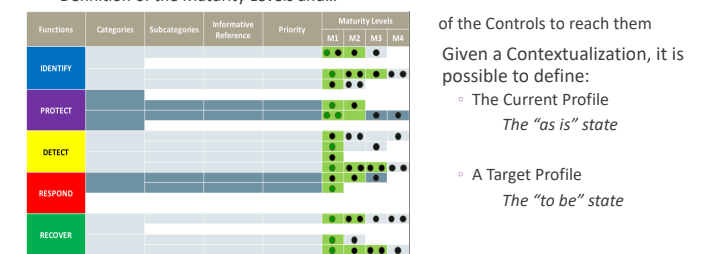
The level of priority was assigned in accordance with a survey and an approval by the final organization in accordance with the domain. The fact that the level of priority assigned to each sub-categories change in accordance with the context makes time consuming the process of contextualization. So a methodology is needed to perform a self-contextualization.
immagine priorità
For each sub-category the provided at least three levels of maturity, the framework provides different options, each option depends on the specific context. Going from the first level to the three there is an increas on the level of complexity in the management of the process but decrease the time of obtain information.
immagine maturity levels
It can happen that for specific sub-categories there is just the level 1 and the maximum level.
3.1.1. Contextualization
It is the capability of the framework to be adapted to a particular domain. For each contextualization the first step is to start from the sub-categories and understand (based on the context to formalize) what is relevant and what is not. Once the sub-categories are fixed the priority levels will be defined; at least the maturity levels are defined, only at the end is possible to perform the gap analysis.
Contextualization is the creation of a specific profile for specific sector.
A contextualization can be defined for:
- A single organization, projecting the framework in your own domain.
- An entire economic/productive sector
- Groups of organization based on the scale. For example in small and medium enterprises respond and recover parts are not economically viable in general
- Organizations belonging to regulated sector. Organization which are subjected to specific regulations and laws, like the financial sector.
- Critical Infrastructure
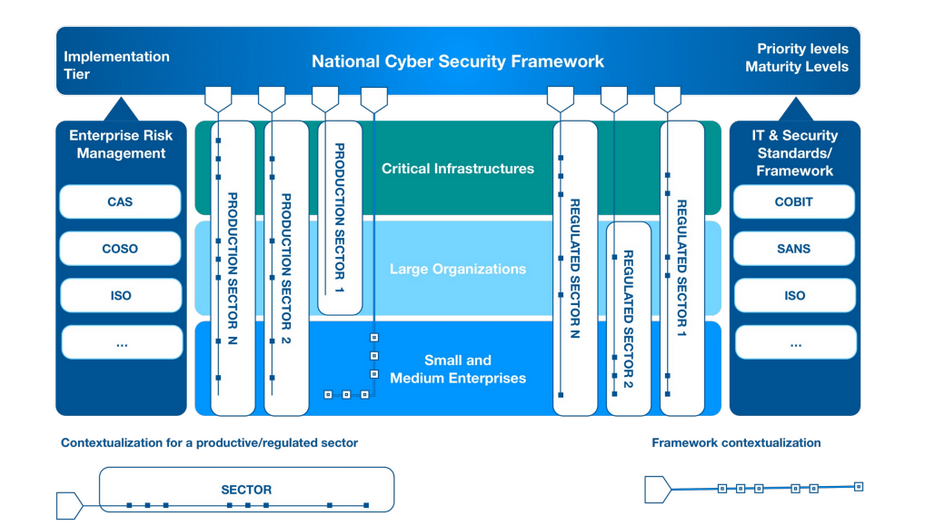
In summary it can be used to adapt the framework, quite easily to almost every context, but the creation of contextualization is not an easy task to be performed.
3.2. NCF 2.0
When the NIST framework was updated some things were improved:
- 61 improvements in the descriptions
- 17 in the core part
- Added one category (supply chain)
- ten new sub-categories
Also the NCF was improved, including also the new GDPR laws, coming out with the version 2.0 of the NCF that provide a new contextualization based on the GDPR.
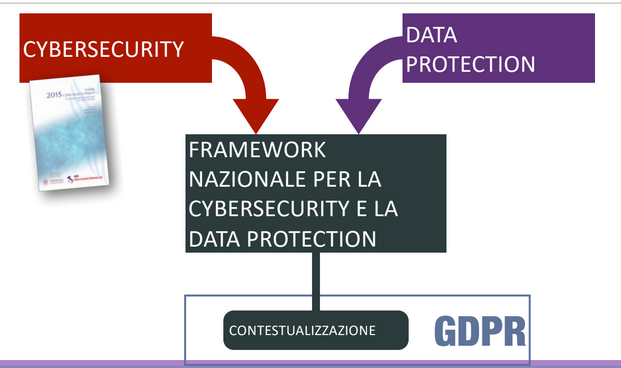
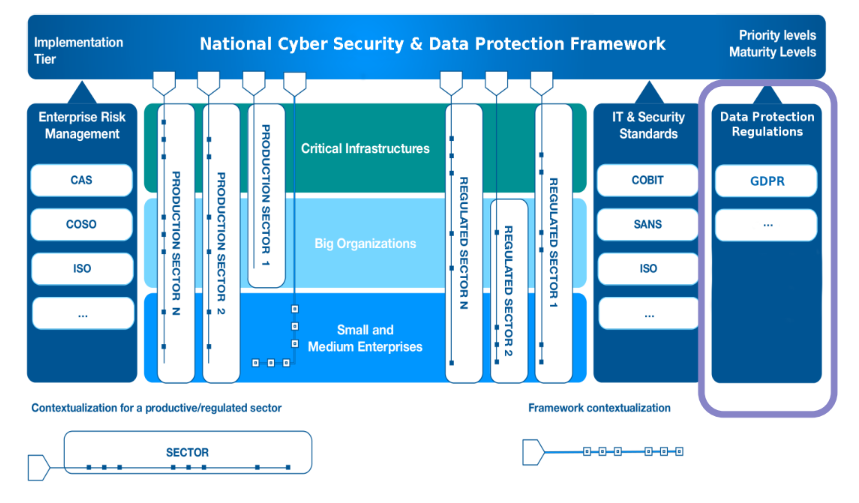
For the second version the researchers worked together with the garanante della privacy office to map the law requirements with the pre-existent sub-categories. Four possible cases:
- Perfect Placement. There was already present a sub-category that can be mapped with one article, more subcategories.
- Partial Placement. There were requirements of the law that were fitting partially with a sub-category, so the regulation was not full covered.
- Not possible placement. In this case there was the need for a new sub-category
- Not needed placement.
So there is not a perfect match between the GDPR and the National Cybersecurity Framework. During the Covid emergence the framework provided a new contextualization for the financial domain, and now they are working on a contextualization for the healthcare domain.
4. Comparison between CSFs.
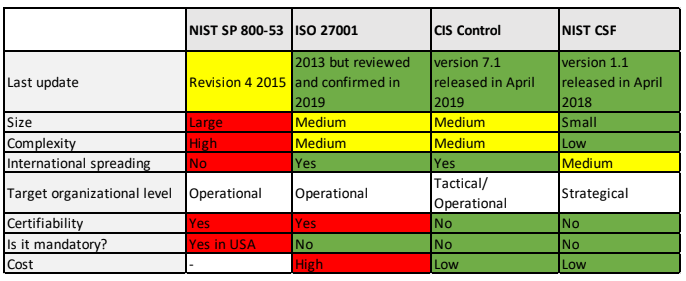
There are three main family of documents: ISO 27k ecosystem, FISMA Ecosystem (United States), SANS 20 (Is more related to the control). The NIST CSF tries to aggregate the information provided by these big families of documents.
4.1. FISMA Ecosystem
It is composed by many different documents, that have been produced starting in 2002 by NIST under the mandate of the United States government. It is the first concrete act that changed the way of how the US reasoned in terms of security. Federal Information System Management Act requires that:
each federal agency develops, documents and implements an agency-wide program to provide information security to all information and information systems that support assets and agency processes, including those provided or managed by other agencies, contractors or third parties.
Before 2002 the information security was not pervasive as it is today. This law triggered different processes and the production of different documents. It was implemented in two phases:
- Definition of standards and guidelines. It lasted more than ten years, producing a large set of documents.
- Implementation and assessments Aids.
4.1.1. Phase 1 Documents
The first two documents produced were FIPS 199 and FIPS 200, they set the minimum level of Information Security that every federal office has to implement. The 800-series is the set of documents that deals with the implementation of the cybersecurity act; we will take a look to the NIST 800-53 that is about Security, Privacy controls for Federal Information Systems and Organizations. All these documents follow directly from the first two. In the US, by law, every federal office must be certified FIPS 199 and FIPS 200. They explain the level of potential impact.
4.1.2. Special Publication 800-53
With is last revision, the n. 5, of 2020, it has the objective to provide a security and privacy controls catalog for federal organizations and IT systems, providing a process to select control to protect mission, functions, Image, Reputation, Assets, Individuals and the State from cyberattacks, disaster, malfunctions and human errors. The document is 460 pages long, and provides 18 control families.
Each control family contains security controls related to the general security topic of the family, and each family is mapped to the ISO 27k documents.
4.1.2.1. Controls
For every control there is the basic claim to be satisfied and additional claims, each one is organized with the following points:
- Control
- Supplemental guidance
- Control enhancements
- References
- Priority and baseline allocation
| Section | Description |
|---|---|
| Control | prescribes specific security-related activities or actions to be carried out by organizations or by information systems |
| Supplemental Guidance | provides non-prescriptive, additional information for a specific security control. |
| Control Enhancement | provides statements of security capability to: (i) add functionality/specificity to a control; and/or (ii) increase the strength of a control. |
| References | includes a list of applicable federal laws, Executive Orders, directives, policies, regulations, standards, and guidelines that are relevant to a particular security control |
| Priority and baseline allocation | Provides (i) the recommended priority codes used for sequencing decisions during implementation and (ii) the initial allocation of security controls and control enhancements to the baselines |
Depending on the target profile, the organization can be certified low, medium or high. The priority and baseline allocation provide guidelines to each level of security.
4.1.2.2. Security Controls Guidelines
The aim of the baseline is to set the minimum level of compliance that you should support for every level selected. Of course it is possible to implement more than the baseline.
4.1.2.3. Limitations
The limitation of the FISMA family is the fact that it is meant for Federal Offices of the United State, so it is very complex and strict. Also it is very technical; so it can’t be used by the strategical level. While outside the US is mandatory by law, but outside the USA it is difficult and it doesn’t have much sense to be certificated.
4.2. ISO 27k
There are many other documents along the ISO 27001 and the ISO 27002 ones. There are also guidance for the auditors, documents specific for the financial services, network security, and incident management. It is the most widespread and internationally recognized world wide. For this reason a recognized entity will be considered certified also in US and on eastern countries. The cons of the ISO 27k family are their costs of the certification, of course it is challenging to small companies to be certified. Most of the time it is used as a self assessment system. Another limitation is given by the fact that the documents do not provide priorities (all or nothing if you want to obtain the certificate). It is not enforced by law.
There exists a mapping between the special publications and the ISO documents, but they are at different level of granularity, so to have a complete overview it is needed to combine them. In any case they are both the result of years of effort of thousand of Cybersecurity experts.