A First Model for Information Security Governance
Table of Contents
1. Second Lecture
- Class: Security Governance
- Topic: Von Solmns Model, ISO 27000, ISPA
- References: von Solms, S.H., von Solms, Rossouw “Information Security Governance” Springer, 2009.
2. Recap on Information Security Governance
The final definition of information security governance from NIST:
The process of establishing and maintaining a framework and supporting management structure and processes to provide assurance that information security strategies are aligned with and support business objectives, are consistent with applicable laws and regulations through adherence to policies and internal controls, and provide assignment of responsibility, all in an effort to manage risk. — NIST
said differently, ISG is the global effort needed to ensure the well-being of the company’s electronic resources.
Investing on security implies employing resources and keep people working on security, so security has a cost, for this reason ISG must ensure cost-effectiveness. It means that we have to find the right balance between the cost of security devices and security training, and the risk to which these resources are exposed. It is important to avoid over-protection, spending a lot of money and resources with a benefit non proportional with the investment. On the other side also under-protection has to be avoid, because it can cause risk to materialize.
A good IT Risk Management strategy is mandatory to implement a good ISG strategy. For this reason we have to use a top-down vertical approach.
3. Von Solmns Model
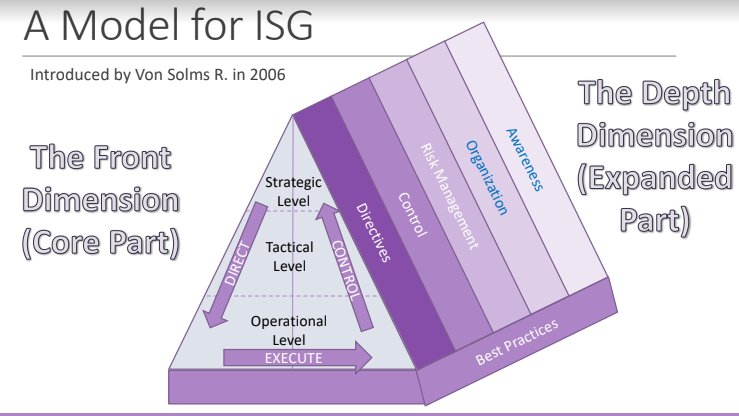
The front dimension, is the core part, then there are the five vertical layers (the expanded part) and the last part is the best practices part.
3.1. Front dimension
It is based in two core principles:
- It covers the 3 well known level of management. Everyone on the pyramid have to be involved;
- Across these three levels, there are very distinct actions. Each level of the pyramid is composed by different actors, with different backgrounds.
So there is the need of technical and economic actors to work together to ensure a good ISG.
3.1.1. Core Principle 1
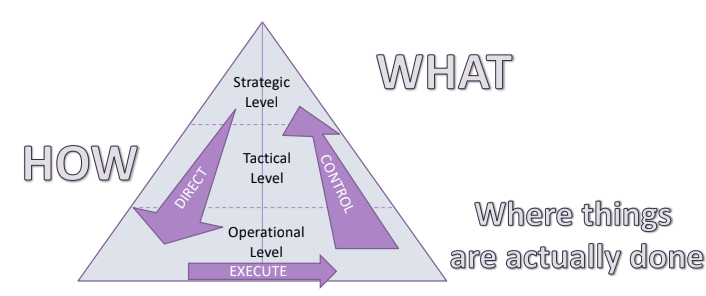
Having different competences, means consider different aspects having different view of security
3.1.2. Core Principle 2
Says that there are three very distinct “actions” across each level. At every level the right amount of information and details has to be outputted.
At the board level, they don’t care about the number of virus detected, but only to know if the company is working correctly and the consequences of the attack (only the consequences).
On the other hand, at the Operational Level the technical information matters.
In general more close to the bottom more the information should be detailed, on the top the information should be aggregated.
3.1.3. The direct part
| Strategic | Tactical | Operational | |
|---|---|---|---|
| What does it means | Identify assets, their relevance and their required level of protection | Directives are expanded into sets of relevant information security policies, company standards and procedure. | Inputs are expanded into a sets of administrative guidelines and administrative procedures and technical measures are physically implemented and management |
| Input | External factors (legal and regulatory descriptors), Internal Factors (company’s strategic vision, IT role, competitiveness) | ||
| Output | a set of directives indicating at high level what the board expects must be done as far as the protection of the company’s information assets is concerned. | policies, procedures and standards | Operating procedures specifying how things must be done. Execution on the lowest level |
The directives simply summarizes the mandate that the strategic level output to the tactical level. At the tactical level, the macro-objectives are translated into policies, that are concrete directions for the implementation. The security policies, internal standards and procedures are outputted into the operational level, the policies are implemented by putting in place the technical parts.
3.1.4. The Control Part
you can only manage what you can measure.
The control part lead to the compliance control. To implement the control part we have to specify that is possible to control only the things that we are capable to measure (in a quantitative or qualitative way); so we have to define a measuring metric for the direct process. In order to verify we need to observe the environment and collect the data, so we have to identify the correct set of data that we want to evaluate.
The measurability characteristic must be at the center of all directives, policies, standards and procedures produced during the ’Direct’ part of the model. Different metrics can be selected at different levels of the pyramid.
| Operational | Tactical | Strategical | |
|---|---|---|---|
| What does it mean at Control at this level | Measurement data is extracted from a wide range of entities. | measurement and monitoring against the requirements of the relevant policies, procedures and standards. | Situational Awareness |
| Input | Measurements | ||
| Output | Specialized reports can be created on this level using this extracted operational data | Tactical Management reports, indicating levels of compliance and conformance | Reports reflecting compliance and conformance to relevant directives including risk considerations |
At the Operational Level the measurement data can be collected automatically or manually, the method of collection depends also on the type of data to collect; for example if the data to measure depends on human / machine interaction the data has to be extracted manually, so it can be biased. An error at this level will propagate and amplify at the top levels. The tactical management receives a detailed report and has to verify if the level of risk observed is compliant with the policies, then produces an aggregated and correlated report to give at the strategical level. The strategic management use the report to perform situational awareness, where the problems are and where it should act. Then a new loop starts, to plan investments or policy editing.
Each iteration of the loop takes months to be implemented. Problems that happens at the technical level can be fixed as fast as possible.
3.2. The Best Practices
The ISG model should help in doing the right things right
The best practices are at the base of the pyramid, and the feed the direct control loop and the vertical part of the model. From the point of view of the security manager there are questions to answer:
- How do I know what the right things are?
- Suppose that I know, how do I know I am doing it right?
A best practice is a general terms that comprehend a big set of documents that tells how you should address some situation considering experience coming from different domains, experts and scenarios. Can be seen as the consensus of experts in the field of Information Security. Many standards exists, and each of them has different scopes and objectives.
- ISO 27000 family.
- COBIT. It is a big manual for management guidelines,
- NIST SP 800-*.
- CSC. Inspired the reference point of Italian Cybersecurity Agency
- NIST CSF
- ENISA
3.2.1. ISO 27002
It is one of the reference document for the ISMS. It is an international standard defined to help companies in selecting controls used to implement correctly ISMS. It contains recommendation on what you should do and in the implementation of the control. The ISO 27001 can be used to obtain security certification. It includes a set of accepted information security controls, helping on the development of the information security management guidelines and self assessment. It is reviewed every 2 or 3 years.
The ISO 27002 is structured in 14 security control clauses, for a total of 35 categories and 114 controls to implement. Each clause gives information about security controls that contains one or more main security categories.
Each main category contains:
- a control objective stating whats need to be achieved
- one or more control that can be applied to achieve the control objective
Each control description is structured as follows:
| Control | Defines the specific control statement, to satisfy the control objective. |
| Implementation guideline | Provides more detailed information to support the implementation of the control and meeting the control objective. The guidance may provides further information that may need to be considered, for example legal considerations and references to other standards. If there is no other information to be provided this part is not shown.to be entirely suitable or sufficient in all situations and may not fulfill the organization’s specific control requirements. |
| Other information | Provides further information that may need to be considered, for example legal considerations and references to other standards. If there is no other information to be provided this part is not shown. |
At the beginning of the standard we have the objective of Management direction for information security: so the first thing is to produce a method to direct the process.
3.2.2. ISO 27001
It is an international standard, that specifies the requirements for establishing, implementing, maintaining and continually improving an ISMS within the organization. It is basically a checklist that is used to check if the control in compliant with the ISO 27002 standards. It is generic and intended to be applicable to all organizations, regardless of type, size or nature.
3.2.3. ISO 27001 and ISO 27002
ISO 27001 is very strict and specific. On the other hand ISO 27002 is more flexible because it gives suggestions and has to be used has a guideline to implement a ISMS.
3.3. Vertical Elements
The vertical elements are five: directives, control, risk management, organization and awareness. They are verticals because they comprehend all three layers.
3.4. Directive
Security Policy documents are required from standards and best practices. Directive layer provides guidelines compliant with the standards. In order to properly support the direct process we need to document all the aspect at the three layers; at each level the right amount of granularity has to be used.
3.4.1. An Information Security Policy Architecture
A architecture is a framework that describe a set of documents. In an ISPA we’ll consider a following set of documents:
- a board-initiated directive concerning information security governance.
- a corporate information security policy, is an aggregator of concepts with a list of references to more specific documents.
- detailed sub-policies following from the CISP. So instead of create a big mess of things to do, smaller documents are produced.
- detail a set of internal standards that we want to achieve, and the documents explaining the detailed procedures to implement the policies.
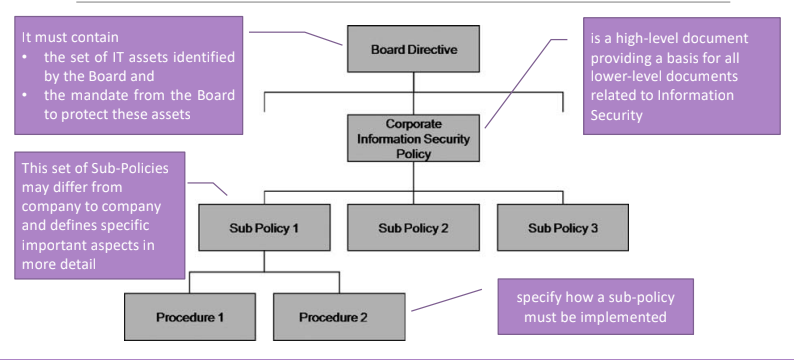
The link are bidirectional, the reason for the bijection is to trace the origin of each policy.
3.4.1.1. The board directive
It must contain the set of IT assets identified by the board and the mandate from the board to protect these assets. A statement that explicitly says what to do. If the statement is not included all the decisions can be interpreted as an imposition by the lower layers.
3.4.1.2. Corporate Information Security Policy
Is an high level document, that provides the common base for the definition of all the policies. It provides generic information about the structure and number of policies. Then it has the pointers to each sub-policy.
Concerning this document there is no a general guideline or structure. But some guidelines has to be respected to create a proper CISP. First of all the CISP must indicate board directive mandates, so it should be clear why we are doing some actions. The CISP must be accepted and signed by a CEO or equivalent officer to be clear that the mandate comes from the top management.
The CISP must not be to long nor technical, it has only to provide a framework; it must contain the high level statement related to the information security. It has to be stable, changing it to much will not lead to a stabilization of the system; for this reason this document has to be technology neutral, and must not contain any references to specific technologies. On the other hand it has to indicate who is the owner of the Policy and what are roles of responsibilities of each person, in this way anyone will be proactive to be more efficient.
The document must also indicate clearly the scope of the policy and why the policy has to be implemented and who will be impacted by it; also it has to specify which disciplinary actions will be taken in case of non-compliance. The CISP document has to be distributed as widely as possible in the company and must be covered in all relevant awareness courses.
The CISP must have a compliance clause for each policy. This is important because each policy has to be verified in the control part of the loop, so how could the policy can be verified and measured. It is a statement that tells the condition that allow to verify if you are compliant or not with the policy.
3.4.1.3. Sub-Policy
Explain in detail each sub-policy, who’s responsible for it and it’s aspects.
The set of sub-policies may differ from company to company, but usually the following ones will be defined for everybody, like: malicious software control policy (anti-virus policy), an acceptable internet usage policy, an acceptable email usage policy, logical access control, disaster recovery backup policy, remote access control policy, third part access control policy and more…
It is very important that the ISPA clearly indicate where these different policies originates, in summary each sub policy must be linked to the CISP.
3.4.1.4. Procedure
It is the more detailed documents that explains how a sub-policy is implemented. It indicates from which sub-policy it follows and it can be a responsibility form.
3.5. Control
An important part in all the documents that are defined in ISG is the part in which there are compliance clauses, they specify what actions we have to take to verify that we are compliant. The compliance clauses will compare in every document we consider, starting from the CISP, down to the sub-policies and procedures.
The definition of the control starts from what are indicated in the standard ISO 27002; in the 18.2 section, the standards says that the ISG has to be compliant with the security policies and standards; so at the end, it is important to define the compliance verification process.
Managers should regularly review the compliance of information processing and procedures, within their area of responsibility with the appropriate security ppolicies, standards and ant other security requirements.
It says that, periodically, you should revise not only the direct part, but also the control part. So the control part has to be monitored to include potentially uncovered camera.
There is no single methodology to define the compliance policy because the definition of a policy if dependent on the context. Given the fact that the policy depends on the context, also the compliance clause depends on it. However there are some guidelines.
First of all we can control only the things that we can measure; typically the measurement process is done by an auditing procedure (verification point by point of correctness); this lead to the notion of auditing the risk, that is related to the ISMG. The general metrics that regulate the Direct Control loop in ISG is the risk.
The risk is a measurement, quantitative or qualitative of the level of security that can be tolerated
It is important to relate, as soon as possible, the compliance clauses to the notion of risk. Of course the concept of risk has different levels of granularity in different layers. The compliance clauses can be used also to estimate the risks, so the two concepts are strictly related and work together.
3.5.1. Issues
When trying to define compliance clauses there are some issues, given the fact that we are implementing a loop it is important to take into account time to manage the loop. If the time is not managed correctly the system will never stabilize because you are giving direction without waiting enough time to observe the consequences (too short loops), or you are too slow in the reaction phase (too long loops).
Also consider that the world is dynamic and monitoring should be done in near real time; because just a moment after a measurement is taken the environment has changed. A solution is to reduce as much as possible the time window of the loop taking decisions not at any iteration but at fixed timestamps.
3.5.2. Guidelines
When defining a compliance clause there are four bullet points:
- The compliance clause should be clear and precise, without leaving any ambiguity (what to check, what to measure and what to verify).
- The compliance should express a way to measure its satisfaction.
In the CISP is preferable to have a clause for each statement.
3.6. Risk Management
The risk management is the third vertical level, and by definition it is:
The process to identify and assess all potential risks as well as introducing controls that should mitigate all these risks to acceptable low levels
From this point of view, the risk could be decomposed in two main variables (two factor risk model):
- The frequency or probability of something bad happens
- The consequences of the issue that may happens
It is possible to act on those two dimension in an join way or a independent way; so we have to identify which is the impact if the bad things happens and how to reduce the probability of the bad event or how to mitigate the effects of the bad event.
Practically speaking we say that the risk can be quantified using the following formula: \(\text{Risk} = \text{Likelihood} \times \text{Impact} = (\text{threat} \times \text{probability}) \times \text{impact}\), representing the risk in a graphical way:
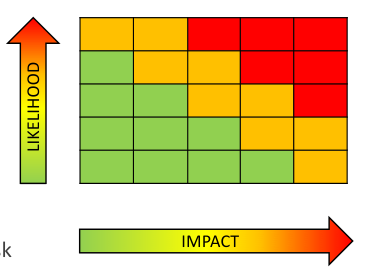
A risk reduction is possible via three actions:
- Reduce the impact, put in place mechanism like replication, redundancy and similar.
- Reduce the probability of the incident, via maintenance for example.
- A combination of both aspects, moving on the diagonal of the heat map.
In the ISO 27002 there is a particular statement that regards the risk management, it says that risk management is essential to identify the security requirements. Potentially all the identified risks create consequences on the company, but practically not all of them could not be managed, mitigate a risk is not cheap: sometimes there can be a direct cost, or there can be indirect cost given by re-training or time consumption.
Not addressing the risk means that you accept that if the risk happens there will be consequences that can cause economic losses (also this is an indirect cost).
In order to work properly in risk management We have to start from the bottom:
- Operational Level quantify the risk in terms of compromission of technical items;
- Tactical Level link the compromission of a machine with the service provided;
- Strategical Level indicate the loss of money and reputation
3.7. Organization
This levels regards the way information security is organized is very important. It is fundamental to structure people to their role and give them the right level of responsibility; the business function have to be organized in a certain way in order to be functional in a direct control process. In ISO 27002 there is some guidelines on Organization of Information Security.
There are two elements to consider, the base: where you physically do the security activities (operational levels), and the part that provides indication and checks if the indication are followed.
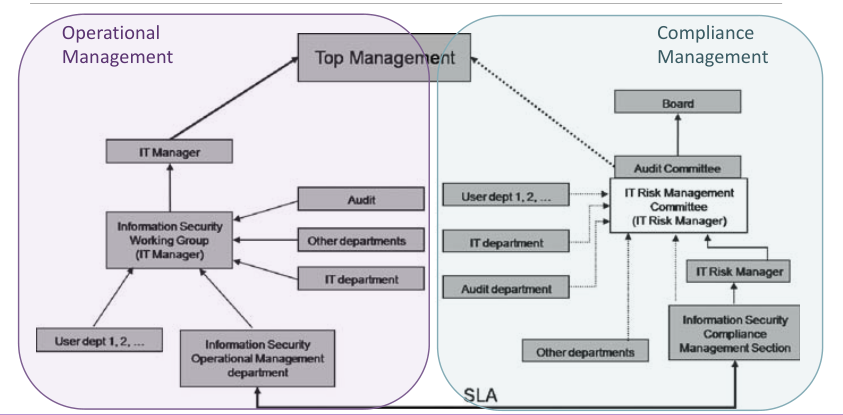
This picture represent how to structure the organization of the Information Security Governance. The operational management (controlled) talks directly with the operational level of the pyramid, in this section we put all the people that actually do something to ensure the protection of the system. The Compliance Management (controllers) is composed by all the people that controls that all the action are compliant with policies and directive and that are actually done.
3.8. Awareness
Awareness start from the top and has to be enforced going bottom, this means that at each level the definition of awareness should change and be appropriate.
- In the Operational Level awareness means being aware of all the policies and of the motivations, communicating the needs and the problems to other employees
- In the Tactical Level awareness means being conscious of the relation between the target settled by the management and what the operational level needs to do.
A global awareness can be established through a SETA program, the aim of this program is to try to train everybody with the purpose of working securely. The objective is to achieve three objectives:
- Awareness, to achieve in the short terms. Gives the notion of what you should do. It is achieved via posters, news letters etc (dissemination)
- Training, it is achieve in medium terms. How to do, via seminars, lectures, and practical exercises.
- Education. Gives the motivation behind the actions.
