#+title: Network Communication
Table of Contents
1. Lecture 11
- Class: Malware Analysis and Incident Forencsis
- Topic: Network
Network Communications are relevant for malware for different reasons, from an analyst perspective, a malware can’t hide its network traces. Today malware may want communicate for different reasons: exfiltration, remote access, botnet. An analyst can gather very useful information by inspecting the network traffic generated by the malware, and at the same time we can came up with new rules for prevention, mitigation and containment of future attacks.
2. Network Countermeasures
Most common approaches to limit infection, or the spread of a malware consits on filtering communications via firewalls and routers, try to resolve domain names to an intern host (sinkhole), or use proxy servers to perform filtering.
The first steps in analyzing a sample should review what you gather from the interaction of the sample with infected systems. The advantage of this approach is that live captured data is the most accurate (because some mwlare detects lab environment), and also real traffic contains information about both ends, without being detected by the attacker.
OPSEC is the set of all the actions that we put in place to hide information, in the malware world OPSEC regards hiding the action of the analyst to the attacker.
2.1. Malware OPSEC
It is the set of activities put in place to prevent adversaries from obtaining sensitive information. Running malware at home may alert attackers. The attacker can identify an analyst sending spear phishing email, and watch for access attempts outside a specific geographic area; design an exploit to log infections, and embed an unused domain in malware, to watch for attempts to resolve the domain.
For example, given an IP address of a C2 server, an analyst can use proxy server, Tor or web-based anonymizers, use ephemeral cloud machines, dedicated VM for research in combination with VPNs.
Speaking of paranoia, even if a caching page is viewed, some links and trackers can be triggered because of the proactive loading.
Querying, DNS/IP info can be acquired by a lot of different sources, some tools are whois and dig, but they will expose your IP address. Some websites query for you the given domain name, or IP address anonymizing the request.
3. Network IOCS
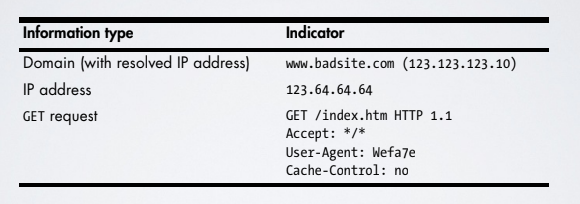
Just with some information, some educate guesses can be made:
- is the domain in a blacklist?
- is the IP address in a blacklist?
- the user agent is quite strange
3.1. Beaconing
Beaocning it’s a first kind of communication that a malware can use to announcing it’s success. The announcement can be done periodical, and when the network is really busy to cloak its presence.
The beacon can contain different info, like the identity of the company attacked, fingerprint of the infected machine.
3.2. Inspecting Traffic
A free tool that can be used to inspect traffic, using a rule based system is snort. An example of a snort rule is:
alert tcp $HOMENET any -> $EXTERNALNET $HTTPPORTS (msg:“TROJAN Malicious User-Agent”; content:“|0d 0a|User-Agent\: Wefa7e”; classtype:trojan-activity; sid:2000001; rev:1;)
You have to write a rule precise enough to capture the behavior, but not to general to have false positives. A good knowledge of the sample is needed.
The analyst Objectives are to coverage fully the functionalities of the malware, and to understand them, including inputs, and outputs.
3.3. Protocol Mimicking
Sometimes malware will mimic existing protocols, often HTTP, HTTPS (to hide the nature and intent of communication), hide information on public pages, or social media posts. Also malware uses user-agents very close to real user agents, or variable, but credible, strings t0 evade detection. Also malware writers tend to use legitimate services to hide communication, like comments on legitimate webpages encoded in base64.
3.4. Identify Networking Code
The easiest thing to do is to loo for the usage of networking APIs, and look for surrounding code. The surrounding code may include random data, data gathered from network libraries, hard coded strings and data, or info about the host and its configuration.
3.5. Identify the Parsing Code
The parsing code will initially check for a starting sequence, perform some consistency checks, and then decode the code (for example from base64) and then stores or execute the command.
Adversaries will diversify their implementation, edit the protocol, and change IP addresses or domains. But some part of the infrastructure are really difficult to change, whenever a network protocol is analyzed, efficient signatures are represented by things that are difficult to change in both the client and C2C, or by peculiar phase of the beaconing, like authentication, and elements of the protocols not immediately apparent.