Malware Evasion
Table of Contents
1. Lecrure 12
- Class: Malware Analysis and Incident Forencsis
- Topic: Malware Evasion
The scope of malware evasion it to remain undetected when under dynamic analysis, so a Malware can be capable of detecting an execution environmental artifact, a sample can deceive even the most sophisticated analysis system.
2. Discrepancies
The first things to look at are the artifacts that comes from virtualization, hardware characteristics, windows installazion, applications, user artifacts, and time overheads and memory footprint.
For example is the machine loos brand new and windows is arleady installed the malware can assume that it is running in a analysis environment.
2.1. Virtualizaiton Aritfacts
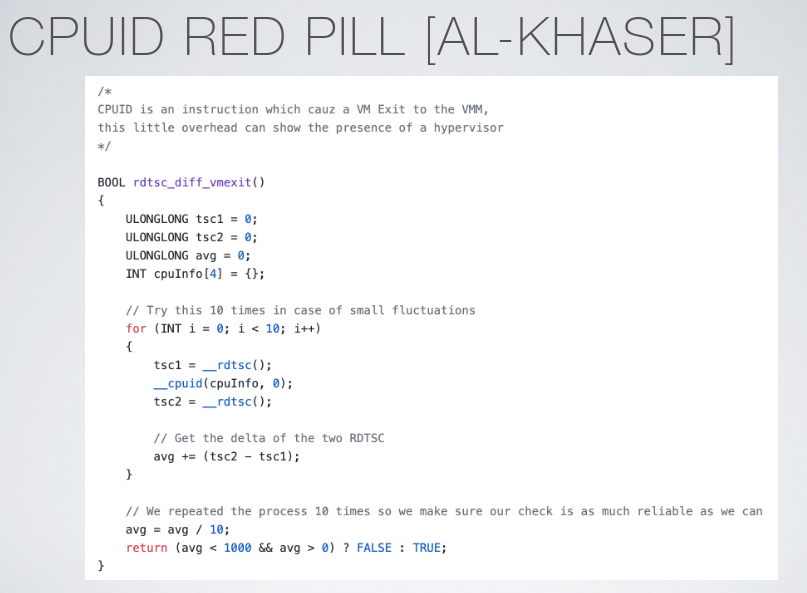
A red pill is an instruction sequence that detects when the code is running on a virutal machine, some instructions take longer to execute when on a hypervisor (cpuid), and instruction errata (incomplete emulation in QEMU) so an instruction when executed will not have the same effect, and I/O ports. For example the malware can try to access hardware directly, trying to identify debug ports for VMs.
cpuid can be slow to execute or show information typical for an hypervisor, other low level information can be system firmaware tables, contents and position in memory of structures, and the microarchitectural state of the machine.
2.1.0.1. CPUID
cpuid retrieve processor identification and feature information and writes to EAX, EBC, ECX, and EDX. Record type is chosen accordingly to the value in eax upon invocation. For example when EAX = 0x1 it writes features information in ECX, thiss will reveal the presence of a hypervisor when the 31st bit is equal to 1. Similarly with EAX = 0x40000000 it writes hypervisor brand information as ASCII bytes forming string like: “KVMKVMKV”, “VMwareVMware”, and “VboxVboxVbox”.
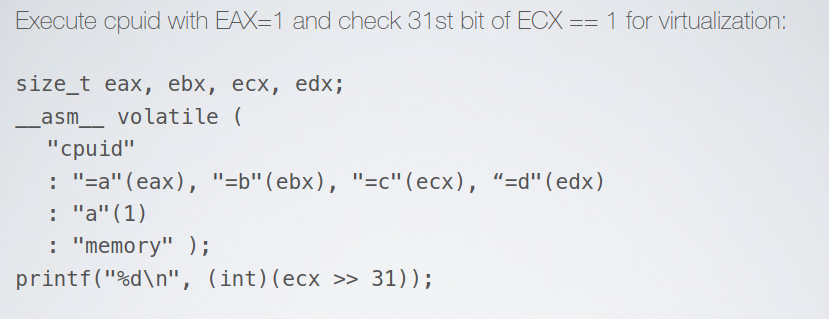
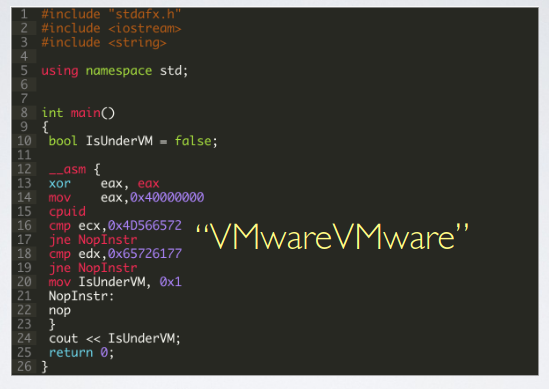
Examples of code that uses CPUID to look for virtualization artifacts.
The VM motiro code is the core of the hypervisor and coordinates the interaction between the host and the guest, this third party will take more time to execute than a normal call of cpuid.
rdtsc is a clock with a very precise resolution, and can be used to check how many cpu ticks have elapsed since the last time before and after cpuid. To do that with high accuracy it is possible to do some manualscheduling.
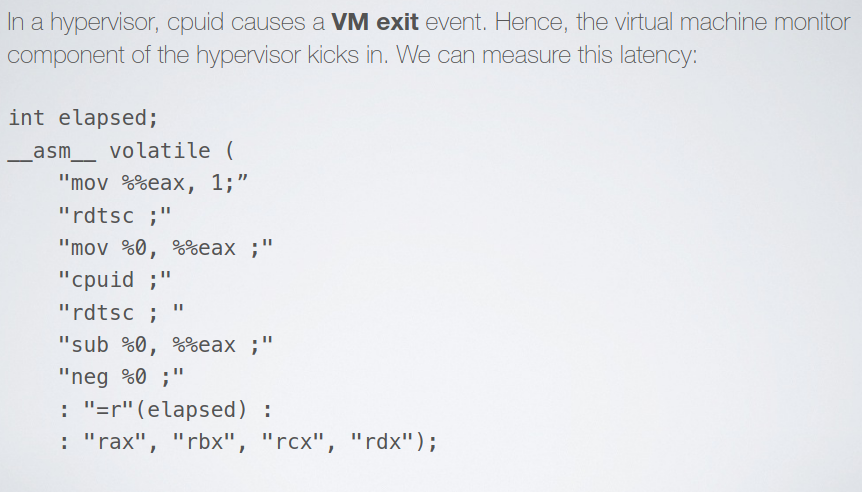
2.1.1. Hardware Characteristics
Some features can reveal a virtual machine, such as CPU model and core count (they can be inconsistent), the number of network adapter and of course the MAC address family (the vendor ID of network cards of VM will be typical). Disk size and serial number of the disk (same as MAC addresses for NICs), check the presence of audio cards, or the capabilities of the audio card (hw support for fast decoding), and of course sensors measurements (fan speed and temperatures).
For targeted malware some of the properties above may be used to check wheter the sampe has met an intnded victim.
Bare metal is good for evasive malware, but not for targeted malware.
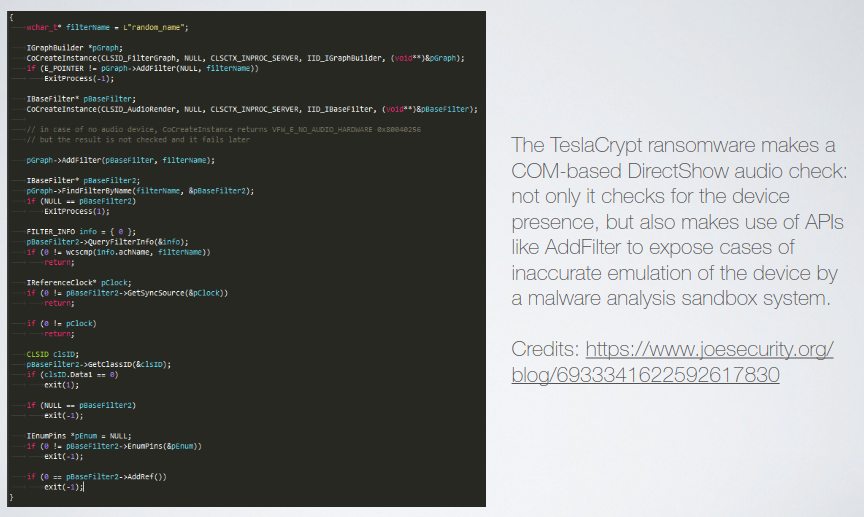
2.1.2. Windows Installation
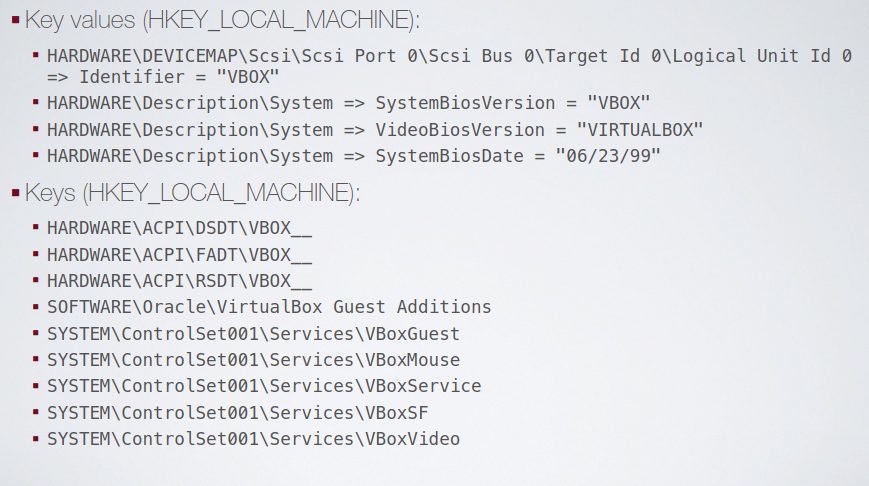
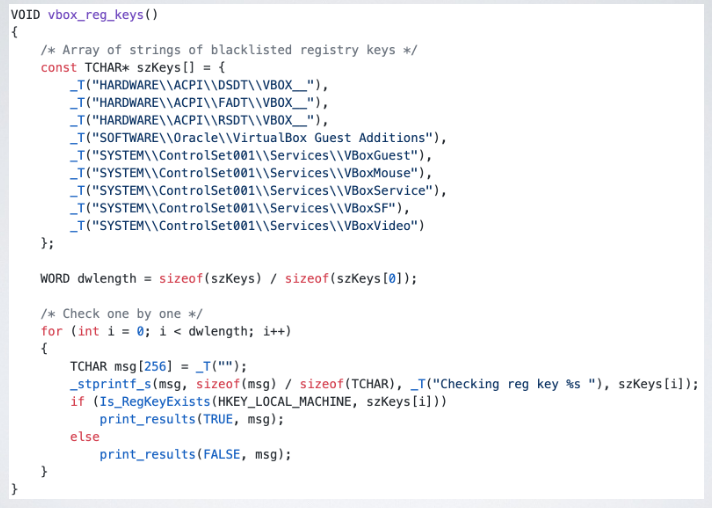
Other helpful stuff for targeted malware is to check the windows machine, timezone, language, the uptime, the install data, and the product key. There also things that impact the window installation, like guest additions composed by registry entries, processes and drivers.
An analyst may be cloack the VM to a good extent, so the basic information that can be catered is masked.
2.1.3. Applications
The malware may check the presence of a specific application, like document reader, antivirus softwarem or a sufficient condition for evasion: like to check if IDA is installed. A software program could be a good reason to trigger a payload, disarm something or evade.
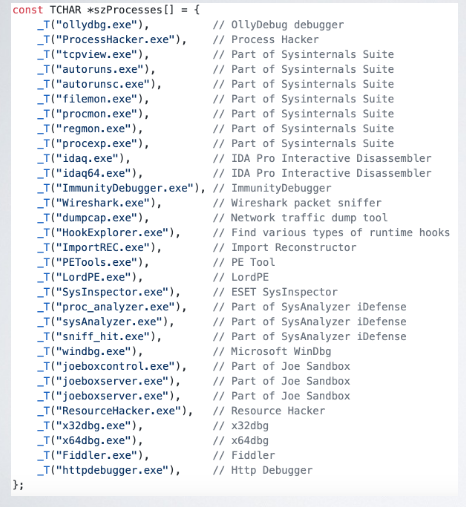
For this reason analyst can use multiple virtual amchine images containing different applications, and versions of those application. Another approach can be to check the presence of injected DLL, typically it used by antiviruses products.
2.1.4. User artifacts
Fresh windows installations are suspicious, other checks are on recently open files, navigation history, lists of usb devices attached to it, number and installation date of applications, number of files in documents folder, and more.
To build a Sandbox a realistic user must be simulated to exhibit a realistic wear and tear state. There are technique that malwares can use to check if the wear and tear state was realistic.
3. What could one monitor?
Consider that there is no such a thing as transparent sandbox. So the analyst can try to fix and hide the artifacts generated, or try to come up with designs that are unaffected by them; sacrificing something (guest addition for example). But how to spot an evasive sequence? They can be spotted by low level instructions like cpuid, int, rdsc, calls to system apis to query system information, a lot of system calls, and WMI queries; and at the end process environment data structures.
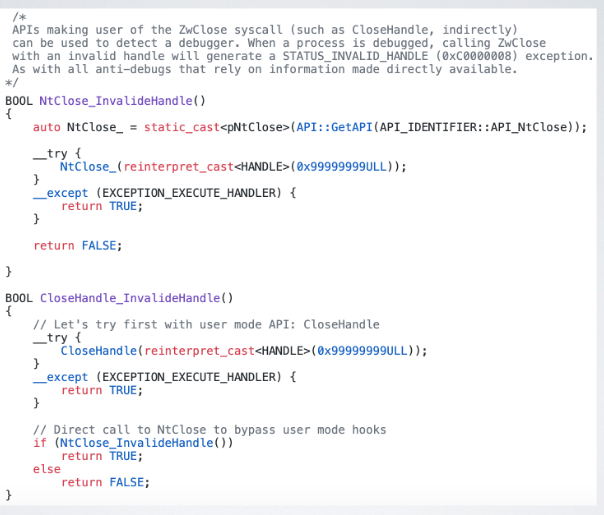
3.1. Anti debugging
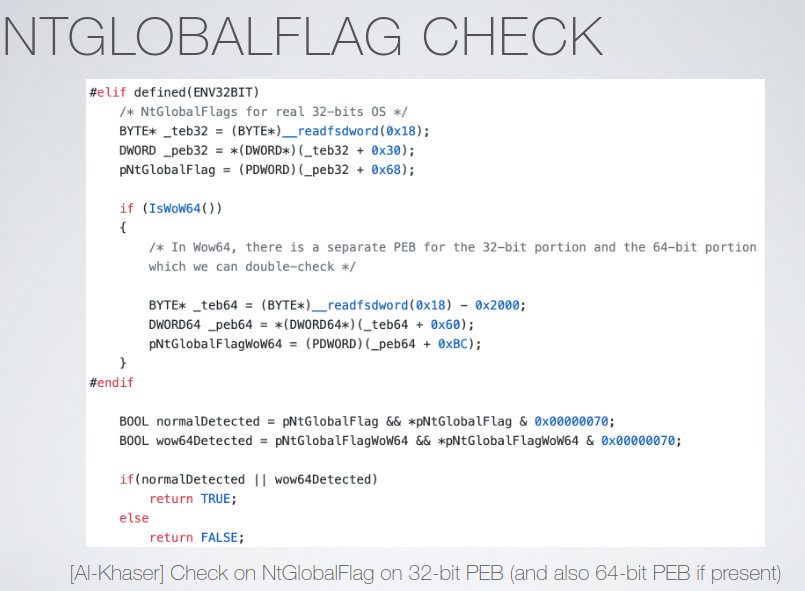
The presence of a debugger alters the normal working of a process, the OS will reveal such effects, directly or indriectly; library functions can be used like IsDebuggerPresent() and CheckRemoteDebuggerPresent(). PEB flags such as BeingDebugged, and NtGlobalFlag; syscalls, and playing with int 2d instruction and other low-level tricks.
3.2. Timing Attacks
A malware can detect, thanks to time, instrumentation techniques used by an analyst, simply by measuring the time of execution. They can make the analysis run out of budget with sleeps, using mulitple sleeps primitives and check if time has been accellerated. Windows offers plenty of time resources to inspect, and malware will check their consistency. The malware can also run very long computations, to buy time.
3.3. WMI
Windows Management Instrumentation enables SQL-Like queries to the OS for enquires about hardware and software.
3.4. In Guest agents.
There are two main attack surfaces, artifacts of the execution technology and artifacts of the software setup; operating inside a virtualized guest is arleady a weakness, so we can modify the hypervisor to perform the monitoring. At the end the problem is that no matter what we do we still share the same execution context of the sample; luckely we can use Virtual Machine Introspection, that enables us to perform the analysis from outside the guest VM. It is a lightweight analysis that provides a good visibility over the memory resisting to both evasion and subversion attempts. It provides:
- Isolation
- Inspection
- Interposition. It is important because, it is possible to intercept any system call, being able to intercept the instrucitons and even modify the results.
A semantic gap problem occurs when trying to inspect high level processes using low level data:
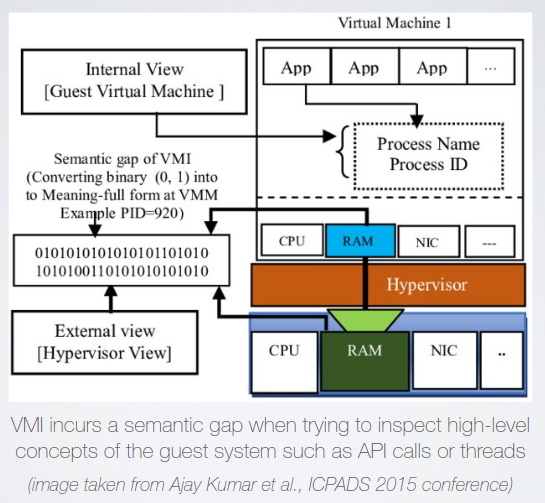
There are open source solutions, like DRAKVUF that solves most of the problems, but when dissection is required VMI is no lifeboat for conspicuos manual work. A growing thread is out-of-VM debugging of a process running in a VM. There are open source solutions, like DRAKVUF that solves most of the problems, but when dissection is required VMI is no lifeboat for conspicuos manual work. A growing thread is out-of-VM debugging of a process running in a VM (Hyberdbg).