Advanced Static Analysis
Table of Contents
1. Lecture 7
- Class: Malware Analysis and Incident Forencsis
- Topic: Static Analysis
2. Advanced Static Analysis
Considering that the sample is not heavely obfuscated or packed using IDA its possible to dissasemble the code and inspect it. The goals are to:
- Identify relevant functions
- understand the behavior
- Extract IoC
2.1. Global and local variables
The main differences is that a global variables can be accessed and used by any function in a program, they may contain configuration parameters or status variables. Local variables can be accessed only by the function in which they are defined. In C this two kind of variables are declared in a similar way, but in assembly they are declared in a differently way:
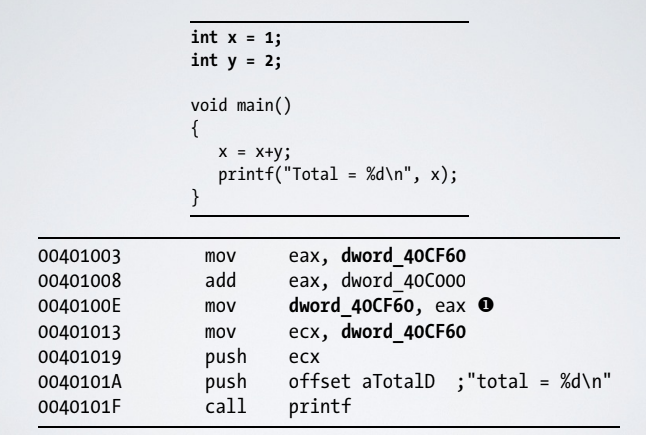
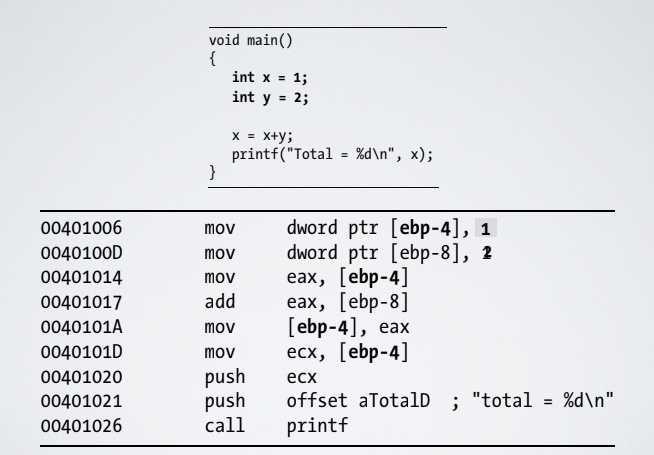
2.2. Arithmetic Operations
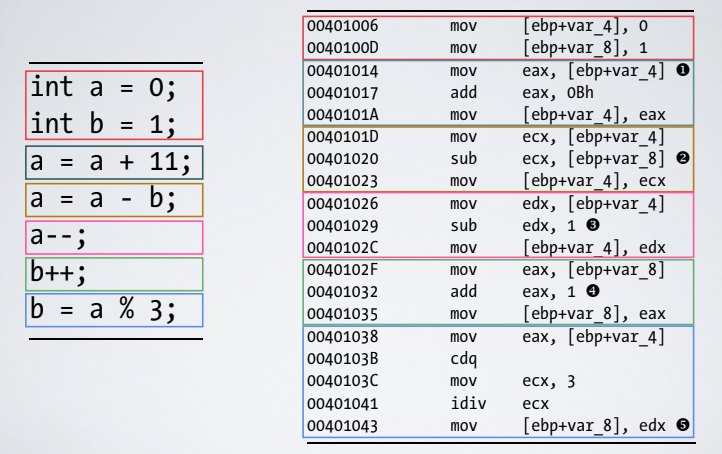
3. PUSH/MOV into the stack
Visual studio uses more the push operation, where GCC uses the MOV operation. When using a MOV its important to make space into the stack via a SUB operation.
4. Windows API
4.1. Hungarian Notation.
Windows API has its own names to represent C data types.
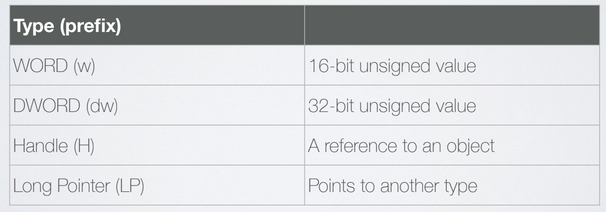
Duplicating handles can be used to pass data between processes.
Transacted files, can be abused by malware. A file can be used as a database, so it is possible to create a transaction to a file without making it permanent, no other process can be aware of the modification: change the library as a transaction, then toss the edit without letting an antivirus spot the malicious code.